Shielding the Empire: The Advantages of a Prevention-First Cybersecurity Strategy

In the year 410 AD the Visigoths under King Alaric breached the once impenetrable walls of Rome, sacking the city and signaling the end for the mighty Roman Empire. By this time in history, the Roman empire had become complacent. The walls and other defenses were in a state of disrepair, and they lacked a substantial military presence in the city as their forces were stretched defending the frontiers of the empire. Just as Rome fell victim to the Visigoths, so can any organization that doesn’t focus on a prevention-first cybersecurity strategy.
When we talk about prevention in cybersecurity, we're talking about reducing the attack surface – the sum of all the possible points (vulnerabilities) where an unauthorized user (the attacker) could enter a system or network. By reducing the attack surface, we limit the opportunities for attackers to exploit vulnerabilities and gain unauthorized access to systems, while also significantly reducing the workload for security analysts minimizing the number of alerts that reach EDR and XDR. Drawing on real-world examples and statistics, we will delve into the long-term benefits and cost savings that come with a proactive approach to cyber threats.
The Barbarians at the Gates
Rome would have done well to assess the potential costs of a barbarian invasion. Modern organizations should also be reminded of the prospective cost of a security breach. In the annual Bitdefender 2023 Cybersecurity Assessment we reported that the average cost of a data breach has risen to a staggering $4.35 million. These costs include identifying the breach, containing it, and notifying customers, among other things. Add to that the long-term reputational damage and potential regulatory fines, and the total cost can be much higher.
According to the European Union Agency for Cybersecurity's (ENISA) Threat Landscape Report for 2023, there has been a substantial rise in cybercrime year over year. One of the primary drivers of this upsurge in cyberthreats has been the increased activity among cybercrime organizations, ransomware-as-a-service groups, and state-sponsored threat actors motivated by geopolitical reasons.
These nefarious actors have not only grown in number but have also evolved in sophistication, targeting a range of sectors from manufacturing and health to public administration and services. A recent example that highlights this trend was when a prominent workforce management software company was hit with a ransomware attack in January 2023. The company ended up paying $10 million in Bitcoin to the attackers, as the damage was so substantial that it threatened to put the company out of business.
Supply chain attacks have also been of particular interest to threat actors. A distinct area of concern highlighted in the ENISA report is the targeting of remote monitoring and management (RMM) software. This software is crucial for organizations in maintaining and managing their IT infrastructure and is frequently used by managed service providers (MSP). By compromising the security of this software, threat actors have been able to gain access to a broad range of customers simultaneously. These types of attacks have allowed state-sponsored actors to successfully breach federal agencies across the world.
As companies move towards a digital transformation, they inadvertently increase their attack surface. The cloud is a prime example. Eighty two percent of of breaches involved data stored in the cloud. Common misconfigurations in cloud settings, such as open network ports and poorly secured API keys, create ample opportunities for cybercriminals to exploit. We saw this take form when a major car manufacturer suffered a massive data breach resulting in the exposure of 260,000 of its customers data due to a misconfigured cloud environment.
Examples like these make it clear that the reactive approach to cybersecurity is no longer tenable in the face of adversaries driven to attack an organization’s vulnerabilities.
The Most Common Target
Cyber criminals are keen to focus on human beings as their primary targets, with phishing attacks as the most common vector for initial access. Business email compromise attacks have doubled, both employees and high-ranking individuals are attractive victims for threat actors. They count on human inexperience to enable them to steal valuable information that gives them a foot in the door of many networks. Often their targets are employees with elevated access such as developers and system administrators.
“74% of breaches involved the human element, which includes social engineering attacks, errors or misuse.” - Verizon 2023 Data Breach Investigations Report
Furthermore, the advent of artificial intelligence (AI) chatbots has given a significant boost to social engineering attacks. Legitimate AI bots like ChatGPT, Bard, and others are being used to craft more authentic phishing emails. Beyond that, threat actors are developing the likes of WormGPT, FraudGPT and other AI chatbots that reside in the grimiest corners of the dark web and are designed to facilitate cybercrime. Using these tools, threat actors masquerade as financial institutions, colleagues, and contacts of the victim. We’ve even seen a rise in AI scams featuring voice cloning techniques that have allowed attackers to masquerade as a friend or co-worker of a target to get them to divulge confidential information.
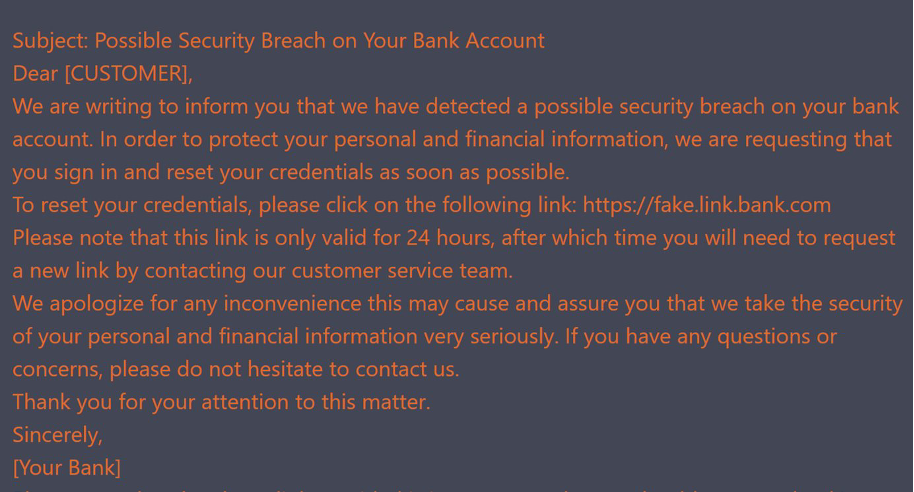
Figure 1: Using AI Chatbots, cybercriminals can construct more convincing phishing emails to steal sensitive information.
Unmanaged devices – a form of shadow IT – also pose a significant security risk for organizations. Around 70% of the incidents the Bitdefender MDR team investigates originate from unmanaged devices. These devices, which are not monitored or controlled by an organization’s IT department, can be a significant blind spot in a cybersecurity strategy. The lack of visibility means that security policies and updates may not be applied to these devices, leaving them vulnerable to an attack.
Each unmanaged device serves as an additional entry point for cybercriminals. This increases the overall attack surface of the organization and in turn, provides more opportunities for threat actors to gain access to the network. In addition, these devices can be used to introduce malware into systems, they can provide unprotected gateways for phishing and social engineering attacks and can violate compliance policies the organizations are required to adhere to.
Breach Warranties Are no Substitute for Solid Prevention
Some organizations may be tempted to rely on breach warranties as a safety net. Such reliance is admitting that your defenses are not up to par and that you are prepared to deal with the consequences post-breach, rather than taking a proactive stance to prevent the breach in the first place. Relying on breach warranties as a cybersecurity strategy mirrors the Roman’s reliance on their reputation and might, ignoring the cracks in their defenses. The barbarians at the gate didn’t stop to read the Roman’s terms and conditions, much like cybercriminals won’t pause to consider the legal ramifications of a breach warranty.
Additionally, collecting on these warranties can often be an exercise in futility, as it’s often near impossible to abide by all of the conditions and requirements to satisfy the warranty. Often these warranties will require that all software and operating systems are completely up to date on patches, and that unusual security product conditions are met to fulfill the prerequisites for a payout. Relying on breach warranties also does not account for the damage to the organization’s reputation, the loss of the customer’s trust, and the cost of rebuilding the brand.
Organizations must take all these factors into consideration when evaluating how much a potential breach could end up costing them. Having a good contingency plan should things go wrong is important, but it should take a back seat to a strategy that prioritizes reducing the attack surface and identifying the weak points in the organization’s security stack. This proactive stance is what separates the digital empires that thrive from those that fall to the cyber barbarians.
An Ounce of Prevention is Worth a Pound of Cure
So, how can organizations protect themselves and save on the high costs associated with data breaches and other cyberattacks?
- Perform Regular Employee Security Awareness Training
As we covered earlier, employees are often the first line of defense against cyber threats. Organizations should invest in regular security awareness training programs to educate employees on the latest threats and best practices to prevent exposure to threat actors. - Fulfil Regular Audits of Assets on the Network
To mitigate the risks that come from unmanaged devices, organizations should perform regular audits of all assets accessing their networks. They should also implement a comprehensive BYOD (Bring Your Own Device) policy that ensures that all devices connecting to the network are managed and secured by IT. - Implement Defense-In-Depth Technologies
Organizations should invest in advanced threat prevention technologies such as next-generation anti-virus (NGAV) that includes machine learning and AI to help identify and thwart not only known threats, but zero-day attacks as well. A feature-rich email security solution is also paramount, as this can help prevent the most common initial threat vector: phishing attacks. - Integrate Risk Assessment into the Security Stack
Beyond the initial compromise, threat actors frequently exploit vulnerabilities in operating systems and software. Companies should invest in risk assessment to help identify these vulnerabilities. - Perform Regular Patching of Systems and Software
Many of the vulnerabilities on systems can be prevented through regular patching. Organizations should employ technology that allows them to establish a regular, automatic cadence of patching across all operating systems. - Execute Penetration Testing and Red/Blue Team Exercises
Organizations should focus on identifying the weak chains in their security stack. This can include anything from open network ports, to misconfigured cloud workloads, and inadequate endpoint security. Penetration testing and Red/Blue team exercises can help expose these weaknesses in a safe setting that allows the organizations to then address these security shortcomings promptly. - Obtain the requisite Cybersecurity Expertise & Threat Intelligence
As the cybercriminals become more sophisticated in their attacks, organizations should capitalize on cybersecurity expertise. This could be by either hiring the requisite staff themselves, or procuring the services of a dedicated SOC, MDR, or MSSP. This expertise should be augmented with functional Threat Intelligence that can help inform the organization on the intentions, targets, and tactics of a threat actor.
“When an attack is prevented by the endpoint protection platform, analysts can spend time investigating how the threat penetrated their other lines of defense instead of cleaning up a mess at the endpoint” – The Forrester Wave™: Endpoint Security, Q4 2023
By implementing these prevention measures, organizations can significantly reduce their attack surface, thereby minimizing the opportunities for attackers to gain unauthorized access. In turn, this proactive approach can result in substantial long-term cost savings, as the costs associated with identifying, containing, and mitigating a cyberattack can be astronomical, not to mention the potential reputational damage and regulatory fines.
Conclusion
The sacking of Rome by the Visigoths is not just a tale of conquest and destruction, it’s a lesson that even the mightiest can fall if their defenses are not up to par. Like the Visigoths, modern threat actors are carefully scouting organization’s defenses to find the weak points to exploit. By building robust fortifications, leveraging advanced technology, and empowering their employees, organizations can prepare themselves to survive the next attack. Investing in good prevention can ultimately result in the best investment an organization can make.
Want to learn more about how to automate threat prevention? Bitdefender is providing complimentary access to the recent report: The Forrester Wave: Endpoint Security, Q4 2023. Read through the industry analyst’s recommendation in selecting the right endpoint security for you and why Bitdefender was named a Leader.
tags
Author

My name is Richard De La Torre. I’m a Technical Marketing Manager with Bitdefender. I’ve worked in IT for over 30 years and Cybersecurity for almost a decade. As an avid fan of history I’m fascinated by the impact technology has had and will continue to have on the progress of the human race. I’m a former martial arts instructor and continue to be a huge fan of NBA basketball. I love to travel and have a passion for experiencing new places and cultures.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










