The Threat Intelligence Requirement

The war against hackers and cybercriminals continues to intensify daily. As hackers become more numerous and sophisticated, organizations require increasingly comprehensive detection, analytics, defense, and remediation tools. Effective defense against cybercrime begins with timely collection and processing of actionable threat intelligence.
CISOs demand better threat intelligence
CISOs consider improving the detection of advanced threats among their highest security priorities, as a recent report by the Enterprise Security Group showcases.
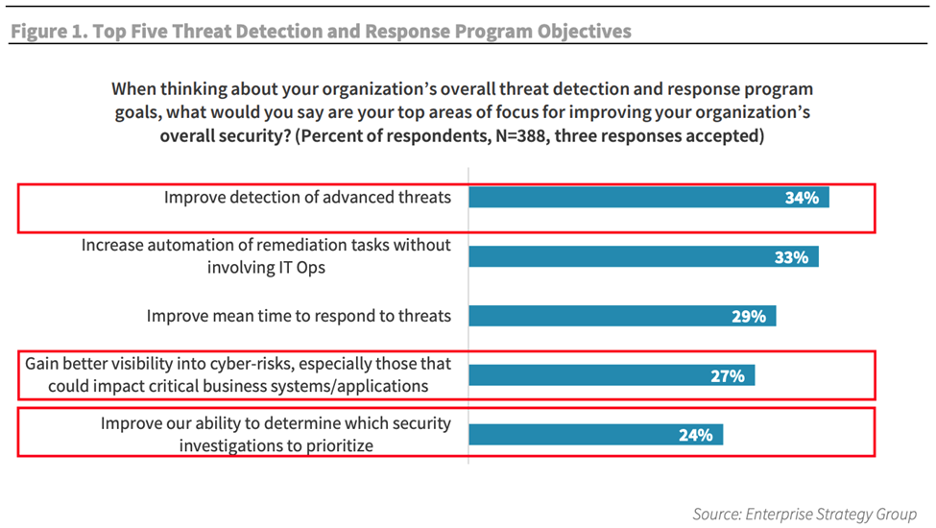
CISOs want to know what tactics, techniques and procedures (TTPs) exist, which ones are most likely to affect their business, and each threat’s potential severity. And they want this information faster than ever.
CISOs and their SOC teams also want to understand better the assets that define the attack surface. Correlating comprehensive real-time threat information against mission-critical assets allows teams to prioritize defense and remediation efforts better. With improved threat intelligence, SOC teams can refine their detection algorithms, improve resource allocation and prioritization, and streamline their security workflows’ overall effectiveness and efficiency.
CISOs want accurate and actionable threat intelligence
Getting the most accurate threat intelligence possible requires data collection from various sources and rapid, high-quality processing. Data gathering efforts must cast a wide net, including sources such as domains, IP addresses, file hashes, etc. First-hand data is crucial because data aggregated by third-party sources can be duplicated and inefficient.
Given increasingly large threat data sets, it is also essential to use curated actionable intelligence, avoiding missed threat identifications and false positives that would waste the SOC team’s time. Automated data processing, amplified by artificial intelligence algorithms, helps deliver immediately actionable information by normalization, de-duplication and categorization of the threat data.
Automation alone, however, may not be enough in certain cases. Organizations also need access to experienced human analysts who can improve automated intelligence effectiveness.
CISOs want operationalized threat intelligence
Comprehensive threat intelligence itself doesn’t save the day, particularly for organizations with limited or non-existent threat analysis resources. Instead, organizations also must be able to use the data quickly and easily. They need systems that can accurately translate threat data provided in a machine-readable format (MRTI) into actionable intelligence that their other security tools can digest to provide automated response and remediation.
Increasingly, organizations are adopting the MITRE ATT&CK framework as a foundation for operationalized security efforts. MITRE ATT&CK provides a comprehensive breakdown of TTPs into categories, allowing organizations to coordinate security efforts against specific TTPs and create “threat-informed defenses.”
The Bitdefender advantage
The ESG report highlights Bitdefender as the preeminent threat intelligence provider. ESG focuses on four areas where Bitdefender sets itself apart from its competitors:
- Data scope: Bitdefender assembles massive amounts of data from numerous sources, from a global network of hundreds of millions of systems to dark web monitoring tools to honeypots and law enforcement, to ensure the most comprehensive collection of threat data.
- Automated processing capabilities: Raw intelligence data has limited usefulness. Bitdefender uses advanced algorithms to identify patterns in the data, helping them isolate threats such as potential ransomware attacks and even highlight specific actors and attack campaigns.
- Elite analysts: Nearly 20% of Bitdefender’s 1600-member global team are highly experienced security analysts, researchers, and threat hunters. The team collaborates closely with law enforcement worldwide on incident response and with prominent academicians to improve data analytics algorithms.
- Robust reputation services: Bitdefender provides organizations with extensive real-time reputation lists in an MRTI format, allowing organizations to quickly block malicious URLs, domains, IP addresses, and file hashes. Organizations can easily integrate Bitdefender’s threat intelligence into existing security response and remediation tools, including security information and event management (SIEM) systems, among others.
Learn more about how Bitdefender’s Advanced Threat Intelligence can provide real-time security insights into the global threat landscape.
tags
Author

Shanice Jones is a passionate business technology writer. She is based in Chicago, USA. For more than five years, she has helped over 20 startups build B2C and B2B content strategies that have allowed them to scale their businesses globally.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











