How Your Neighbour's Cat Could Be Hacking Your WiFi
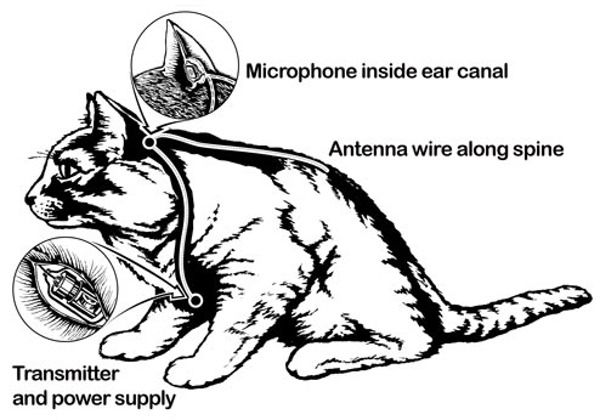
In the 1960s, the CIA ran a top secret project to spy on Soviet embassies… with cats. The project – codenamed “Acoustic Kitty” – involved a battery and small microphone being implanted into a cat, and an antenna put into its tail.
No-one would suspect a cat of eavesdropping on sensitive conversations, wagered the CIA spies. To the relief of animal-lovers, and the dismay of the CIA’s Directorate of Science & Technology, the project flopped.
Exactly why the cat failed to be an effective spy is in dispute – some say it failed to behave as desired, and would be more interested in seeking out food. Others claim it was hit by a Washington DC taxi almost immediately after its release. Whatever the reason, anyone who has ever owned a cat knows that the project was probably doomed from the start – cats simply won’t do what you want them to do. Ever. But that hasn’t stopped others from trying.
At the DefCon conference in Las Vegas last week, a security researcher revealed that he had enlisted the help of his wife’s grandmother’s Siamese cat (named Coco) in an attempt to sniff out poorly-protected WiFi in his neighbourhood. Gene Bransfield, a security researcher with Tenacity, claimed in his talk entitled “How to Weaponize your Pets”, that some 15% of internet traffic is cat-related. So maybe he’s onto something.  Thankfully, Bransfield’s top priority was that the cat should not be harmed. Instead, he asked his wife’s grandmother to sew a comfortable leopard-print collar which Coco could wear, and stuffed it with technology to record the feline’s GPS waypoints as it slinked its way around neighbouring houses, scanning WiFi to collect SSIDs and other data for later analysis.
Thankfully, Bransfield’s top priority was that the cat should not be harmed. Instead, he asked his wife’s grandmother to sew a comfortable leopard-print collar which Coco could wear, and stuffed it with technology to record the feline’s GPS waypoints as it slinked its way around neighbouring houses, scanning WiFi to collect SSIDs and other data for later analysis.
 Bransfield dubbed the collar, WarKitteh – a play on the term “wardriving”, the act of hunting for WiFi networks while on the move. Sure enough, Coco came home with a ton of data about nearby poorly-secured wireless networks – and a dead mouse.
Bransfield dubbed the collar, WarKitteh – a play on the term “wardriving”, the act of hunting for WiFi networks while on the move. Sure enough, Coco came home with a ton of data about nearby poorly-secured wireless networks – and a dead mouse.
The Guardian reports that in total the cat discovered 24 unique WiFi hotspots on its travels – four of which were completely open with no password required to log on, and another four which use the much-derided and frankly useless WEP encryption standard. (Editor’s note: If you’re still thinking your WiFi is secure because you have WEP encryption enabled, think again. It’s time to switch to a stronger standard such as WPA2).
To be frank, Bransfield’s use of Coco the cat is just a gimmick. He could have found the same data out by wandering around his neighbourhood by foot (although the people living next door might have raised an eyebrow if they saw him in their back garden scrabbling up the fence…)
But, although the issue of poorly-secured WiFi has been known for a long time, there are still an alarming number of people who haven’t learned to properly protect their wireless networks, as Bransfield’s research proves.
Bransfield says that it’s important to catch the imagination of the general public in order to get them to take serious action to protect their privacy. “It`s been a failure of the industry and of DefCon-like hackers to appropriately communicate this stuff to people,” he said. “We need to do a better job of communicating this stuff… You don`t want to scare the shit out of them. You want to effectively communicate to them what the issues are.”
Well, he and Coco the cat have certainly caught our attention. Let’s hope more people take security seriously when they hear about this amusing stunt.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
Beware of Scam Emails Seeking Donations for UNICEF or Other Humanitarian Groups
December 19, 2024
Torrents with Pirated TV Shows Used to Push Lumma Stealer Malware
November 14, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









