Malicious SDK Spies on iPhone Users and Steals Ad Revenue, Researchers Claim
Security researchers have uncovered malicious behavior in a software development kit (SDK) used by over 1,200 apps in Apple”s App Store, with a combined monthly user base of approximately 300 million. Researchers claim the SDK steals ad revenue and exfiltrates user data to servers controlled by its developers.
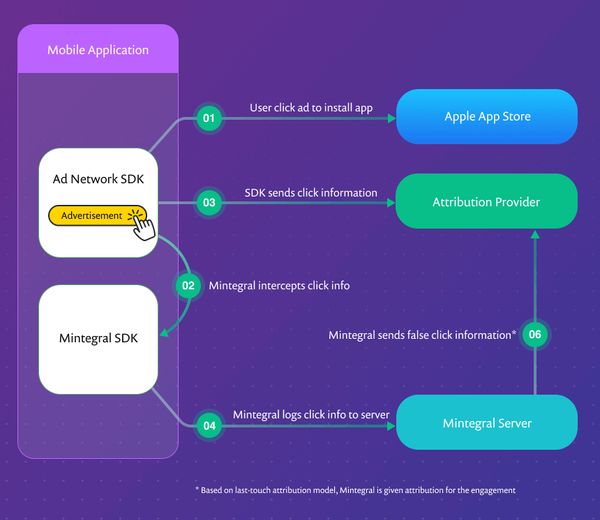
Dubbed “SourMint” by Snyk researchers, the SDK is provided by Chinese mobile ad platform provider Mintegral. It allegedly contains malicious code that can spy on user activity by logging URL-based requests made through apps that have it baked in for ad monetization.
“This activity is logged to a third-party server and could potentially include personally identifiable information (PII) and other sensitive information,” Snyk researchers explain in a blog post. “Furthermore, the SDK fraudulently reports user clicks on ads, stealing potential revenue from competing ad networks and, in some cases, the developer/publisher of the application.”
Mintegral allegedly uses two methods to steal revenue from competing ad networks. By claiming attribution for clicks that did not occur on a Mintegral presented ad, the SDK can steal advertiser revenue that should have gone to the other ad networks.
“This seems to be the main goal of this malicious functionality,” the researchers argue.
The second method is less direct. The research team argues that the developer or mediator SDK may notice that Mintegral is performing better than other ad networks, causing positive bias toward Mintegral. Furthermore, competing ad networks can lose revenue even when Mintegral isn”t used to serve ads, as the malicious code intercepts the clicks even if the service isn”t enabled to serve ads.
“In this case, ad revenue that should have come back to the developer or publisher via a competing ad network will never be paid to the developer,” according to the researchers.
The Mintegral SDK”s malice apparently goes even deeper. It allegedly also contains several anti-debug protections to hide its true purpose.
“In the code, there is a particular routine that attempts to determine if the phone was rooted and if any type of debugger or proxy tools are in use. If it finds evidence that it is being watched, the SDK modifies its behavior in an apparent attempt to mask its malicious behaviors. This may also help the SDK pass through Apple”s app review process without being detected,” the team notes.
The full research is available here. Researchers also provide what they believe is compelling evidence that the SDK exfiltrates more data than it should, potentially including personally identifiable information. The research also includes technical exploit details and remediation.
Of note, Mintegral offers the SDK to Android developers as well. However, according to the Snyk team, the malicious code is only present in the iOS version of the SDK.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
Beware of Scam Emails Seeking Donations for UNICEF or Other Humanitarian Groups
December 19, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








