Ransomware attack attempted to destabilize our country, says outgoing Costa Rican president

Costa Rica's outgoing president, Carlos Alvarado Quesada, has said that a ransomware attack on the government's computer systems was an attempt to destabilize the country as it transitions to a new administration.
The notorious Conti ransomware group has claimed responsibility for an attack that hit six public institutions in Costa Rica last week, demanding that a $10 million ransom be paid to prevent exfiltrated data from being leaked onto the internet.
Amongst those affected by the attack were the Ministry of Finance and the Treasury's customs platforms - with the hackers accessing sensitive historical data related to taxpayers, and causing bottlenecks in imports and exports that are thought to have cost hundreds of millions of dollars already.
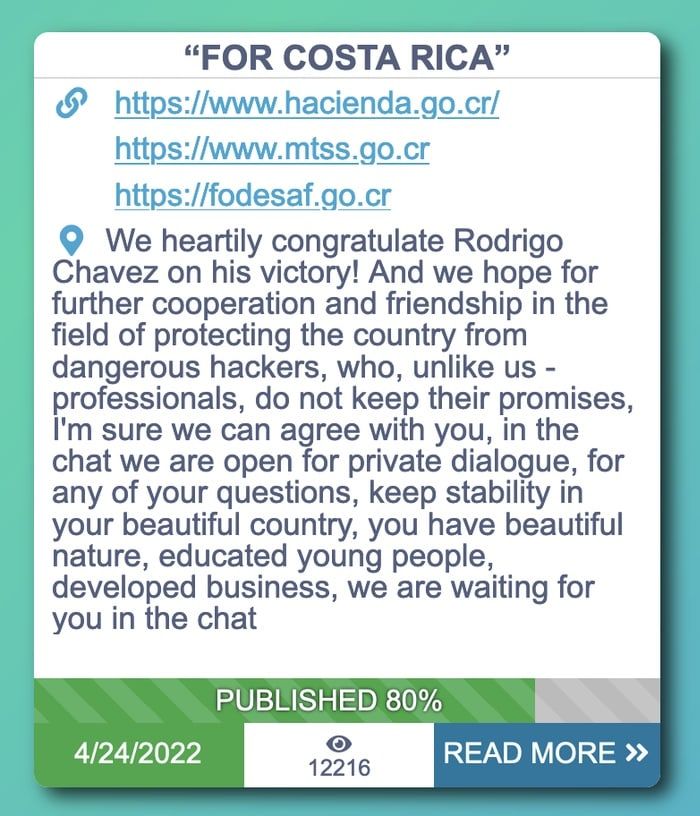
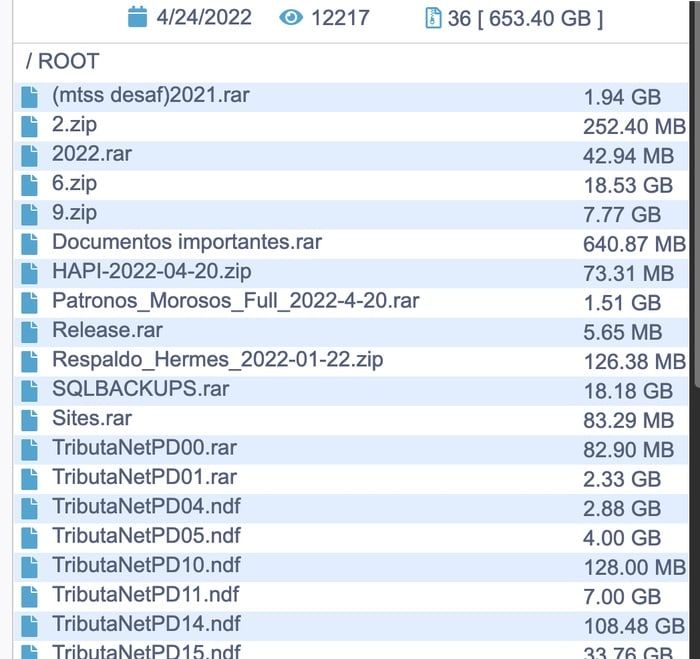
The Conti ransomware group announced the breach on its leaks website, and over the last few days has been releasing more and more of the stolen data.
Alvarado, who leaves office in early May to make way for president-elect Rodrigo Chaves, released a video statement, discussing the attack.
https://twitter.com/CarlosAlvQ/status/1517212653520891905
Alvarado declared that the country would not make any ransom payments to its extortionists, but made clear that he did believe that the attack was not merely motivated by money:
"It is not just an attack on the institutions affected, the government or importers and exporters. It is a criminal cyberattack on the state and the entire country. It cannot be separated from the complex global geopolitical situation in a digitalized world."
Costa Rica's Finance Ministry has warned citizens to be on their guard against phishing attacks, bogus phone calls, and other attempts by criminals to commit fraud following the data breach.
The Finance Ministry says it has been contacted by members of the public who have received tempts have already been seen bogus messages claiming to come from the government, trying to trick recipients into handing over their passwords.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
Genshin Impact Scam Alert: The Most Common Tricks Used Against Players
December 05, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks