Researchers find bad bots designed for account takeover on 100% of websites with login pages
Locking out a “user” after too many failed login attempts should be a best practice by anyone who owns a website with a login field or subscription form, if a new research is any indication. Fraudsters are using elaborate – but predictable – techniques to execute account takeover (ATO) attacks for a variety of nefarious purposes.
Bad actors are engaging in ATO attacks to validate sets of login credentials, gain access to credit card data, and sell personally identifiable information on the dark web. They also use the stolen account data to transfer money, purchase goods, and even spread a specific political agenda, according to data gathered by Distil Networks.
By analyzing 600 domains that include login pages, researchers found that “all monitored login pages were hit with bad bot traffic, indicating that every website with a login page faces Account Takeover (ATO) attempts.”
Other key findings include:
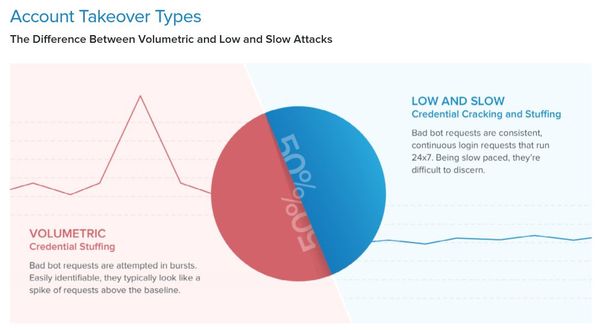
- 50% of ATO attacks come in the form of volumetric credential stuffing, where bad bot requests are easily identifiable and attempted in bursts
- 50% of ATO attacks are through low and slow credential stuffing and credential cracking – consistent, continuous login requests made at a slow pace to avoid detection
- Websites experience a 300 percent increase in volumetric attacks after credentials from a data breach are made public
- One fifth of all analyzed attacks were preceded by a smaller scale “test round” a few days prior, which is considered purposeful by bot operators, but it”s also key element in the attack cycle that renders the attack predictable
- Bot operators schedule attacks when it is presumed that fewer security professionals will be around to notice anomalies, namely on a Friday or Saturday
Website operators are offered a few mitigation tips, such as: block or captcha-secure outdated user agents/browsers; block known proxy services and exposed APIs; evaluate traffic sources and investigate traffic spikes; keep an eye out for one-too-many failed login attempts; monitor increases in failed validation of card numbers; and consider employing a bot mitigation tool.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
Beware of Scam Emails Seeking Donations for UNICEF or Other Humanitarian Groups
December 19, 2024
Torrents with Pirated TV Shows Used to Push Lumma Stealer Malware
November 14, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








