Android Malware in COVID-19 Clothes Steals SMS and Contacts

Criminals are using an old certificate to sign a malware that takes advantage of the COVID-19 pandemic situation, preying on people’s need for information. The goal is to steal personal data, including SMS messages, call logs, contacts, and more.
The COVID-19 pandemic is exploited by bad actors however they can, and no opportunity is wasted in spreading malware.
People look for answers during trying times, and sometimes they install disreputable applications from unknown sources on their phones. Unfortunately, since it doesn’t come from an official store, which typically scans for malware before allowing its publication, the application ends up on people’s phones with ease.
It’s unclear how this particular app is disseminated, but there’s always a risk when installing apps from untrusted sources. An infostealer is just one of the methods used by bad actors to infect Android devices. To protect themselves from this kind of threat, people should use a security solution with its signatures up to date.
Sideloading apps is dangerous
Sometimes, people choose to install apps that are not available in their region or any official store, opening their system up to malware that will steal private data.
There are four different versions of this malware, detected as “Android.Trojan.InfoStealer.UQ”. The package name is “DZ.Eagle.Master” and the app label is simply “Covid”.
The applications have the same label, but the icons are different.


APK MD5
2d84a8bbd77aee8432742dc28eef2da3
4271184bc33ee9672fe4713f14e43bd6
51a4472a506795e386906541c3483080
a81c5c3da9d41069af9ab00780dbe09e
When the user runs the application, nothing happens; it just opens and closes quickly, but in the background, there’s a lot of activity. First, the malware contacts the Command & Control (C&C) and sends the device’s info, including the network operator, phone model, manufacturer, SIM serial number, the Wi-Fi IP address and the Internet IP address.
The C&C sends back a settings.xml file, which it stores in its assets folder
<?xml version="1.0" encoding="utf-8"?>
<XML>
<HP Host="flyrosebifr[.]webhop[.]me">1954</HP>
<Fdir Pkd="DZ.Eagle.Master">Covid</Fdir>
</XML>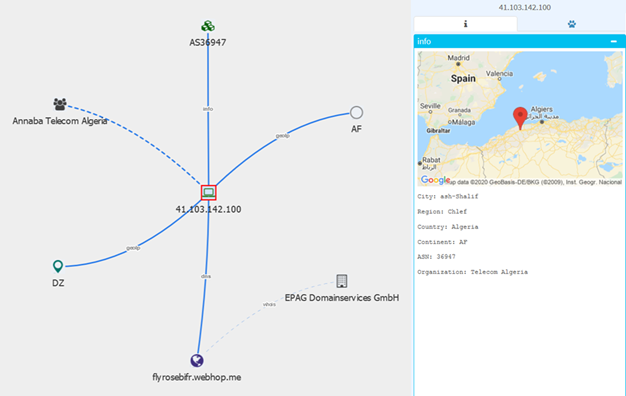
The malware seems to target Algerians, as the package name DZ.Eagle.Master, contains the Algerian DZ country code, and the CnC domain was resolving to a server hosted in Algeria at one point.
This takes us to command processing, and it looks like its developers have separated the commands into five distinct types. While all the samples share the Trojan, some are more advanced than others.

CP – collects all contacts from the device and send them to CnC
Call – phone calls and send them to CnC
Info – device information and send it to CnC: simOperator, phonetype, networkType, networkOperatorName, model, manufacturer, SIM serial number, wifi_ip, ip
MSG – displays a toast message
CL – close command (will sleep for 11 milliseconds), then closes itself)
SMS – spies received SMS – if any exists else ‘No Sms Found :)’.
A curious aspect of the app is that users would have to reboot the phone before the malware goes into full effect, which is likely a means of hiding its actual functionality.
Jawa Barat certificate strikes again
The threat uses the old but still valid Jawa Barat certificate. The certificate was leaked years ago by its developer and is now used to sign repackaged samples with PUA, Adware or malware components.
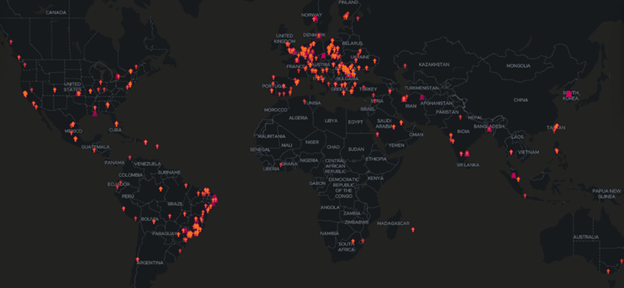
Because the certificate wasn’t revoked, it’s still heavily used in apps and malware. Our telemetry found it in 125,000 scans in 2020 alone. As you can see, the certificate detection is spread all over the globe.
Similar to a previously investigated malware, in which the malware authors left a suspicious text ([SPY_NOTE_VERSION_OK]) in the application version name, in this infostealer the authors left the version name “–no-version-vectors.” It’s a common tactic with polymorphic malware that’s always changing features to avoid detection.
It seems that the Coronavirus trend has sparked the interest of another old malware campaign, as this is the first time this old maliciously used certificate is seen associated with the coronavirus, the gift that keeps on giving.
COVID-19 remains a source of inspiration for bad actors looking to trick people into installing their apps. Users should always be wary of apps that use a coronavirus-theme and always use a security solution to keep their devices safe.
tags
Author
Silviu is a seasoned writer who's been following the technology world for more than two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks











