Inside Bitdefender Labs’ Investigation of a Malicious Facebook Ad Campaign Targeting Bitwarden Users

Throughout 2024, Bitdefender Labs has been closely monitoring a series of malvertising campaigns that exploit popular platforms to spread malware. These campaigns use fake advertisements to lure users into installing malicious software disguised as legitimate apps or updates.
One of the more recent campaigns Bitdefender Labs uncovered involves a fake Bitwarden extension advertised on Meta’s social media platform Facebook. The campaign tricks users into installing a harmful browser extension under the guise of a security update.
Key findings include:
- Platform Exploitation: Attackers are leveraging Facebook’s advertising platform to deliver ads that look legitimate but lead to a malicious website.
- Impersonation of Reputable Brands: The campaign impersonates Bitwarden, a popular password manager, to build trust and create a sense of urgency by prompting users to install a supposed "security update."
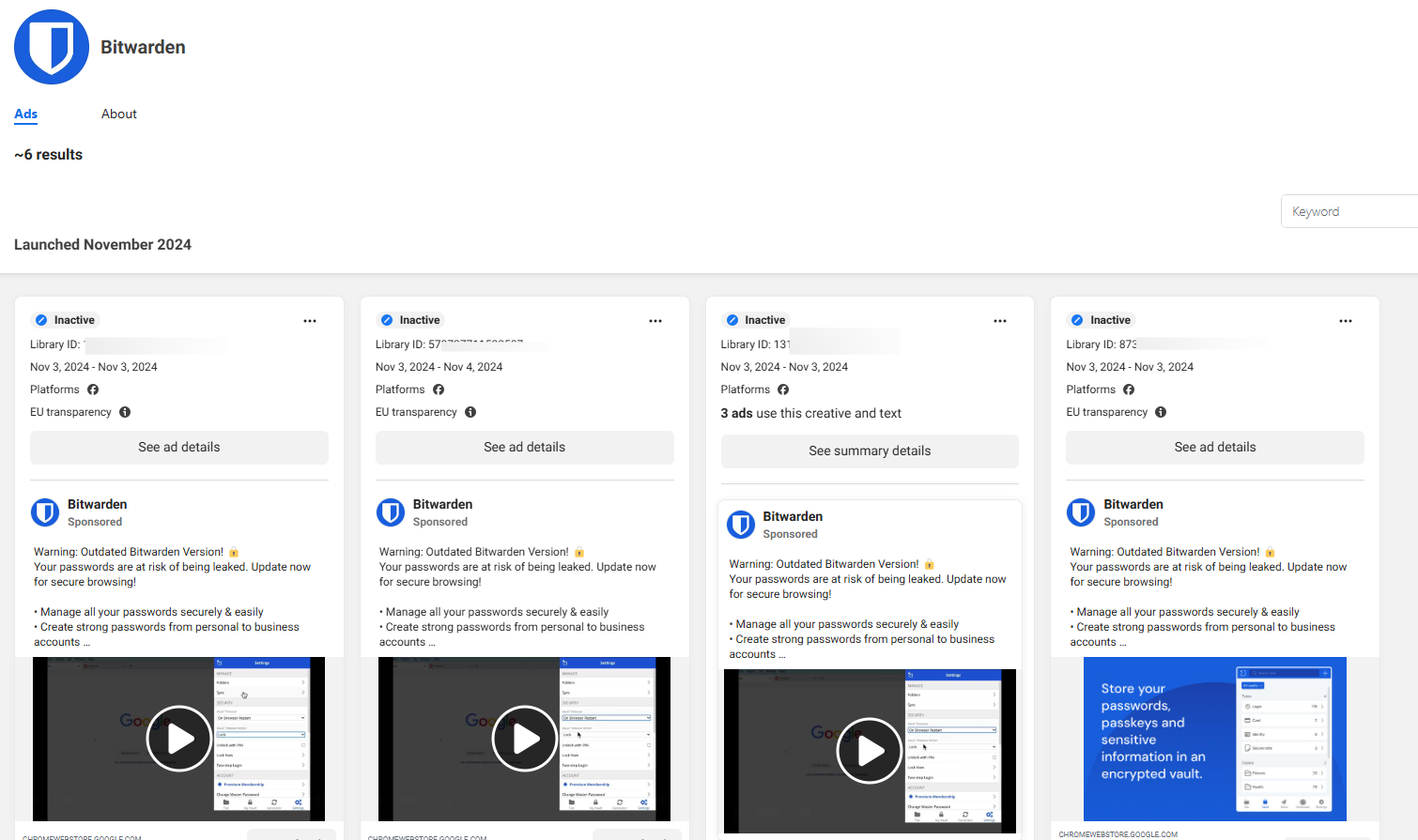
- Specific Target Demographics: Launched on Nov 3, 2024, this campaign specifically targets consumers aged 18 to 65 across Europe.
- Current Reach and Global Expansion Potential: The malicious ads have already been served to thousands of users, and could expand further. If left unchecked, this campaign could scale globally, affecting users worldwide.
- Use of Redirect Chains: Users who click on these ads are redirected through multiple sites, ultimately landing on a phishing page that mimics the official Chrome Web Store to obscure the ad’s malicious intent.
- Data Collection on Business and Personal Accounts: The malware gathers personal data and targets Facebook business accounts, potentially leading to financial losses for individuals and businesses.
Once again, this campaign highlights how threat actors exploit trusted platforms like Facebook to lure users into compromising their own security. By masquerading as a reputable tool and imitating urgent update notifications, cybercriminals gain access to valuable personal and business information.
Thanks to Bitdefender Labs’ research, we now have a clearer understanding of the evolving tactics used in this type of attacks:
1. Step One: Fake Ads to Lure Users In
The attack begins with a deceptive Facebook ad that warns users that their passwords are at risk and urges them to update their Bitwarden browser extension. The ad looks legitimate, using Bitwarden branding and urgent language, such as "Warning: Your Passwords Are at Risk!" to push users into action.
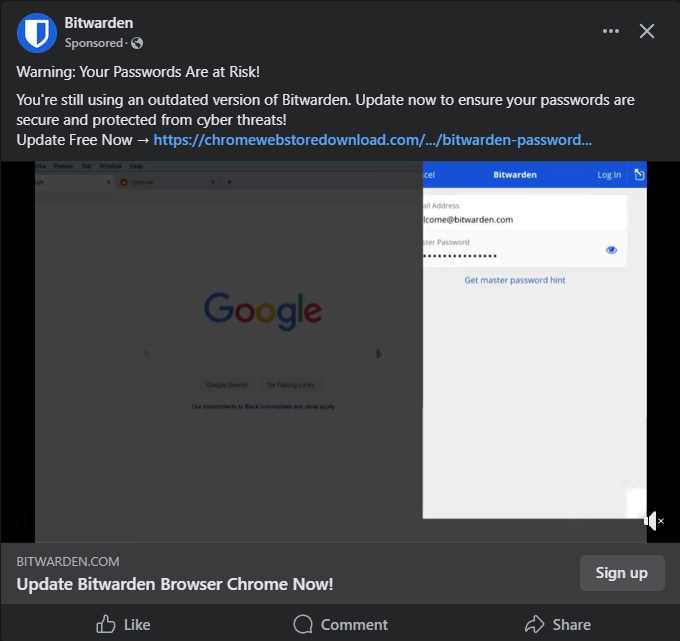
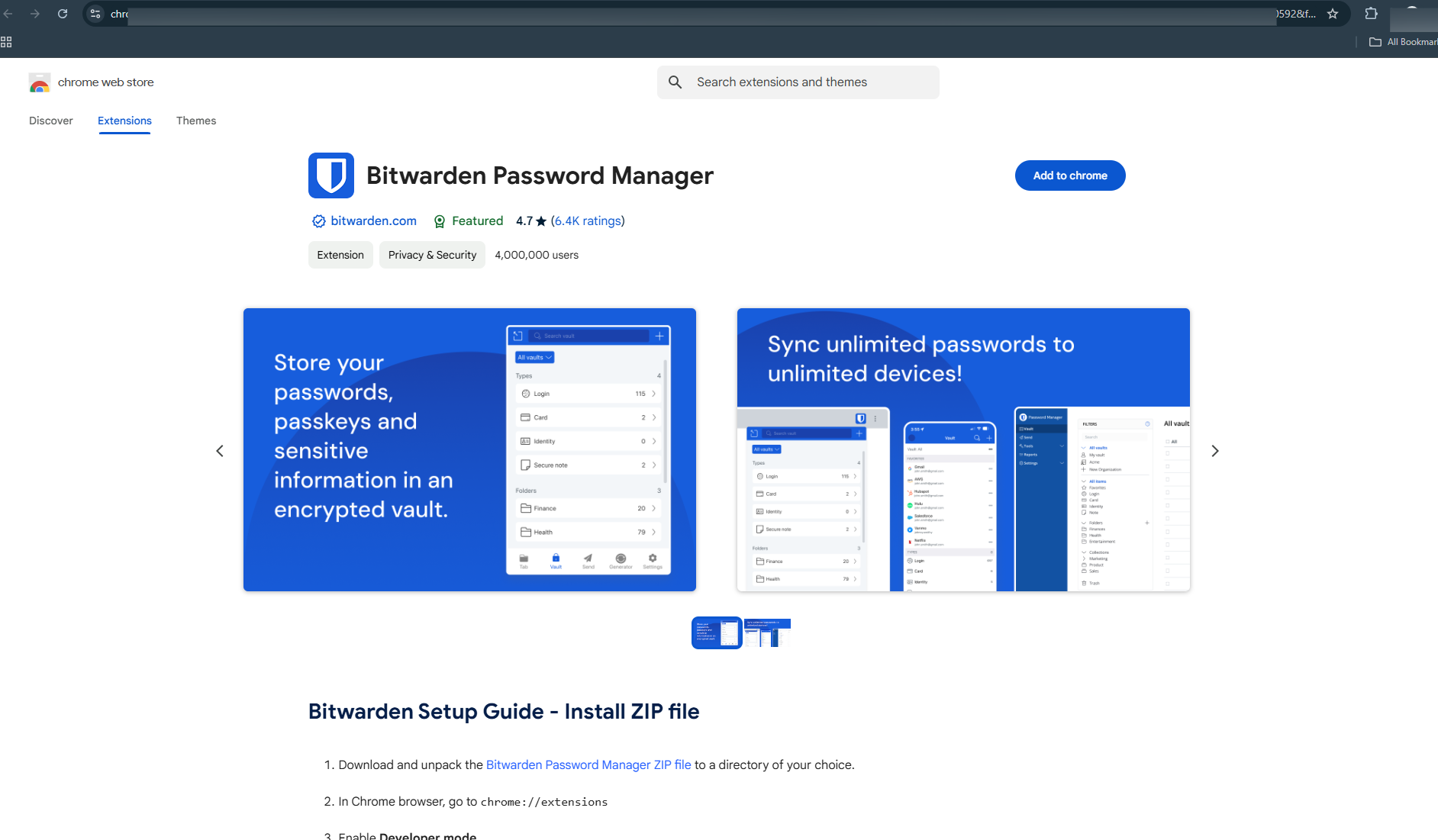
Clicking on the ad takes users to a fake webpage designed to mimic the official Chrome Web Store. When users click "Add to Chrome," they are redirected to a Google Drive link containing a zip file with the malicious extension. Attackers guide users through a process to install the extension by:
- Unzipping the file
- Going to their browser’s extension settings via chrome://extensions
- Enabling Developer Mode
- Manually loading the unpacked extension (sideloading).
This method manipulates users into bypassing browser security checks, allowing the malware to install without detection.
2. Malicious Extension Details: Full Access and Suspicious Permissions
Once installed, the malicious extension requests extensive permissions that allow it to intercept and manipulate the user’s online activities. A closer look at the extension’s manifest file reveals permissions to operate on all websites, modify network requests, and access storage and cookies. Key aspects of the manifest include:
{
"name": "Bitwarden Password Manager",
"version": "0.0.1",
"manifest_version": 3,
"background": {
"service_worker": "service-worker-loader.js",
"type": "module"
},
"permissions": [
"contextMenus",
"storage",
"cookies",
"tabs",
"declarativeNetRequest",
"webNavigation",
"webRequest",
"management"
]
}
The extension’s service-worker-loader.js script initiates background.js, the primary component driving the malicious operations. Additionally, popup.js—an obfuscated script—loads when users click the extension icon in their browser, enabling it to:
- access cookies from https://facebook.com, specifically seeking the c_user cookie containing the Facebook user ID.
- manipulate the page’s DOM elements to display fake loading messages, creating an illusion of legitimate actions.
3. Background Worker: Collecting and Exfiltrating Data
The background.js script, which activates upon installation, is the core of this attack.
chrome.runtime.onInstalled.addListener(async details => {
getFacebookCookies();
});
Here’s how it operates:
- Cookie Harvesting: Upon installation, background.js calls getFacebookCookies() to check for Facebook cookies. If found, it gathers further data using the collectData() function.
- IP and Geolocation Data Collection: The extension queries IP and location data via https://api.ipify.org and https://freeipapi.com.
- Facebook Data Extraction: Through Facebook’s Graph API, the malware retrieves user data, including:
- Personal details like user ID and name
- Business accounts and ad account information
- Credit card and billing details associated with ad accounts
Once collected, the data is sent to a Google Script URL, which acts as the command-and-control (C2) server for the attackers. The sendData() function handles data exfiltration by encoding and transmitting sensitive information.
4. Detection and Defense Strategies
Detecting and mitigating this attack is a challenge for cybersecurity teams due to its reliance on legitimate platforms like Facebook and Google Drive. Here are some detection ideas for security professionals:
- Monitor Suspicious Permissions: declarativeNetRequest and webRequest permissions, paired with access to cookies, are strong indicators of potential malware.
- Behavioral Signatures: Obfuscated functions like chrome.runtime.onInstalled.addListener and calls to graph.facebook.com APIs can serve as indicators of compromise (IoCs).
Safety Tips for Users
To protect yourself from similar malvertising campaigns, follow these essential security tips:
- Verify Extension Updates: Always update extensions directly through official browser stores (e.g., Chrome Web Store) rather than by clicking on ads or third-party links.
- Scrutinize Ads and Links: Be cautious of sponsored ads on social media, especially those calling for immediate action or updates for security tools.
- Check Extension Permissions: Before installing or updating an extension, review its permissions. Extensions requesting access to cookies, network requests, or all website data may be malicious.
- Enable Security Features: Use browser security settings, such as disabling Developer Mode when not in use, to prevent unauthorized sideloading of extensions.
- Report Suspicious Ads: If you encounter misleading or malicious ads on social media, report them to the platform to help prevent the spread of similar attacks.
6. Use a Security Solution: Protect yourself from malvertising and phishing attacks by using a reliable security solution like Bitdefender Total Security. A comprehensive security solution detects and blocks malicious links, phishing attempts, and unauthorized browser extensions, adding an extra layer of protection.
Pro tip: Use Bitdefender Scamio to deter scams and malicious ads.
Bitdefender Scamio is a must-have scam detection tool for netizens who want to steer clear of scams and malicious ads while browsing or interacting on their social media feeds. Scamio is our FREE on-demand scam detector you can use to check for any scammy link or proposal you see online.
Scamio can analyze any texts, messages, links, QR codes, or images and give you a verdict on whether they are part of a scam. Scamio is available on Facebook Messenger, WhatsApp, your web browser and Discord.
Let’s see what Scamio had to say about the ad:
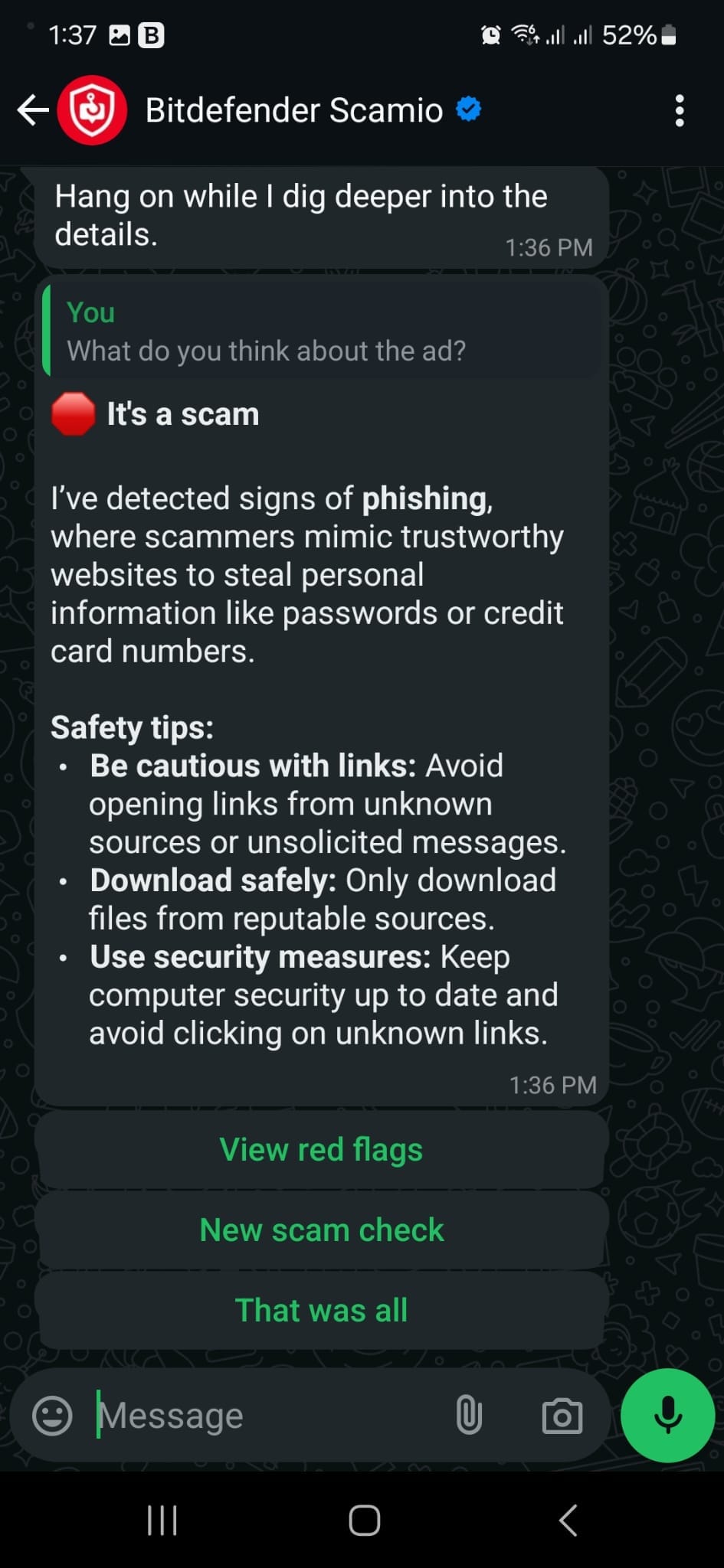
You can also help others stay safe by sharing Scamio with them in France, Germany, Spain, Italy, Romania, Australia, and the UK.
Additionally, with the launch of our new Scam Copilot, you can get comprehensive scam protection across all of your devices with access to your personal scam adviser chatbot, scam wave alerts in your area, real-time detection of scams in your browsing activities and remote access scam protection among others. The Scam Copilot features paired with our award-winning anti-malware protection can be found in our all-one-security solutions.
tags
Author

Andrei is a graduate in Automatic Control and Computer Engineering and an enthusiast exploring the field of Cyber Threat Intelligence.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks















