MaMoCrypt Ransomware Decryption Tool

We’re happy to announce the availability of a new decryptor for MaMoCrypt, a strain of ransomware that appeared in December last year.
MaMoCrypt is an unusual piece of ransomware, a variant of MZRevenge written in Delphi and packed using mpress.
If you don’t want to go through the technical analysis, you can jump straight to decryption by downloading the utility below:
Download the MaMoCrypt decryptor
Ransomware behavior
1. MaMoCrypt deletes shadow volumes, disables the firewall and UAC. These features are nothing unusual in the malware universe, and we will not go into further details.
2. Using Delphi’s random generator (based on a linear congruential generator) and a DWORD seed based on time (using QueryPerformanceCounter or GetTickCount), it will generate two buffers which will be base64 encoded and prepended with MZRKEYPUBLIC / MZRKEYPRIVATE
3. Based on these two keys and a mask (see more details below), it will generate two encryption keys per file, which will be used for encryption. The content will be first encrypted with AES 128 CBC and then re-encrypted with Twofish 128 NOFB. The remainder % 16 from AES encryption will be encrypted using AES 128 CFB. All encrypted files will have their name appended with “.MZ173801”.
4. After encryption, the malware iterates the encrypted folders again to place the ransom note in them. The note will also contain the 2 MZR keys.
Although the MZR keys will not be changed during key generation or encryption, the mask will be continuously updated. Their generation is based on a mix of SHA1, SHA512, and some custom computations. The AES and TWOFISH keys are computed by using SHA512 16 times for each key and XORing the bytes, using the result as the n-th byte of the key.
Mask and keys generation replication:
*(int*)mask_in = offset;
for (int i = 0; i < 0x800; ++i) {
SHA1(mask_in, 0x84, mask_out);
*(int*)mask_in = i + 1 + offset;
*(mask_in + 3 + (i & 0x7F) + 1) ^= mask_out[0];
mask[i] = mask_out[1];
}
offset += 0x800;
aes_key = generate_key(mask, mzrkey_private.c_str(), 0x800, mzrkey_private.size());
for (int i = 0; i < 0x200; ++i) {
SHA1(mask_in, 0x84, mask_out);
*(int*)mask_in = i + 1 + offset;
*(mask_in + 3 + (i & 0x7F) + 1) ^= mask_out[0];
mask[i] = mask_out[1];
}
offset += 0x200;
twofish_key = generate_key(mask, mzrkey_public.c_str(), 0x200, mzrkey_public.size());
generate_key:
int mzrkey_size_bswap = _byteswap_ulong(mzrkey_len);
int mask_size_bswap = _byteswap_ulong(mask_len);
for (int i = 0; i < key_SIZE; ++i) {
((int*)in)[0] = _byteswap_ulong(i);
for (int j = 0; j < i; ++j)
in[j + 4] = key[j];
*((int*)(in + 4 + i)) = _byteswap_ulong(1);
*((int*)(in + 8 + i)) = mask_size_bswap;
memcpy(in + 3 * sizeof(int) + i, mask, mask_len);
memcpy(in + 3 * sizeof(int) + mask_len + i, &mzrkey_size_bswap, 4);
memcpy(in + 3 * sizeof(int) + mask_len + 4 + i, mzrkey, mzrkey_len);
SHA512(in, mask_len + mzrkey_len + 4 * sizeof(int) + i, out);
for (int j = 0; j < SHA512_DIGEST_LENGTH; ++j)
key[i] ^= out[j];
}The IV for AES CBC will be generated using AES 128 ECB on a 16-byte buffer filled with 0xFF. Similarly, the IV for TWOFISH NOFB will be generated using TWOFISH 128 ECB on a 16-byte buffer filled with 0xFF. The initial contents of the mask are generated as follows:
memset(mask_in, MASK_IN_SZ, 0);
memset(mask_out, MASK_OUT_SZ, 0);
for (int i = 0; i < 0x80; ++i) {
SHA1(mask_in, 0x84, mask_out);
*(int*)mask_in = i + 1;
*(mask_in + 3 + i + 1) = mask_out[0];
}We have some bad news, though: because of improper configurations, the ransomware will only use the low DWORD of a file’s size and therefore, any file larger than 4GB will be permanently damaged. In short, only the remainder % 4GB will be encrypted and written, as seen in the image below.
Apart from using an encryption scheme never seen in other ransomware, the binary will also not encrypt the entire system by merely iterating files, but it has a hardcoded list of folders and drives:
C:\Program Files\Steam
C:\Program Files (x86)\Steam
[DRIVES A-Z, WITHOUT C]
C:\Users\%user%\AppData\Roaming\Microsoft\Windows\Recent\
C:\Users\%user%\Pictures
C:\Users\%user%\Music
C:\Users\%user%\Videos
C:\Users\%user%\Documents
C:\Users\Public\Documents
C:\Users\Public\Videos
C:\Users\Public\Music
C:\Users\Public\Pictures
C:\Users\%user%\Downloads
C:\Users\%user%\Favorites
::{645FF040-5081-101B-9F08-00AA002F954E} (Recycle Bin)
C:\Users\Administrator
C:\Users\Public
C:\Users\Default
C:\Users\%user%\Desktop
C:\Users\Public\Desktop
C:\Users\%user%\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar
C:\Users\%user%\AppData\Roaming\Microsoft\Windows\Start Menu
C:\ProgramData\Microsoft\Windows\Start Menu\Because the mask/key generation uses an offset that is incremented at each file, the decryption process is heavily dependent on the files’ encryption order.
The ransomware will only encrypt files whose extension matches one of the below:
.cs;.lnk;.mp3;.jpg;.jpeg;.raw;.tif;.gif;.png;.bmp;.3dm;.max;.accdb;.db;.dbf;.mdb;.pdb;.sql;.dwg;.dxf;.c;.cpp;.cs;.h;.php;.asp;.rb;.java;.jar;.class;.py;.js;.aaf;.aep;.aepx;
.plb;.prel;.prproj;.aet;.ppj;.psd;.indd;.indl;.indt;.indb;.inx;.idml;.pmd;.xqx;.xqx;.ai;.eps;.ps;.svg;.swf;.fla;.as3;.as;.txt;.doc;.dot;.docx;.docm;.dotx;.dotm;.docb;.rtf;.wpd;
.wps;.msg;.pdf;.xls;.xlt;.xlm;.xlsx;.xlsm;.xltx;.xltm;.xlsb;.xla;.xlam;.xll;.xlw;.ppt;.pot;.pps;.pptx;.pptm;.potx;.potm;.ppam;.ppsx;.ppsm;.sldx;.sldm;.wav;.aif;.iff;.m3u;.m4u;
.mid;.mpa;.wma;.ra;.avi;.mov;.mp4;.3gp;.mpeg;.3g2;.asf;.asx;.flv;.mpg;.wmv;.vob;.m3u8;.mkv;.dat;.csv;.efx;.sdf;.vcf;.xml;.ses;.rar;.zip;.7zip;.dtb;.bat;.apk;.vb;.sln;.csproj;
.vbproj;.hpp;.asm;.lua;.ibank;.design;.aspx;.bak;.obj;.sqlite;.sqlite3;.sqlitedb;.back;.backup;.one;.pst;.url;.onetoc2;.m4a;.m4v;.ogg;.hwp;.HWP;.OGG;.M4V;.M4A;.ONETOC2;
.URL;.PST;.ONE;.BACKUP;.BACK;.SQLITEDB;.SQLITE3;.SQLITE;.OBJ;.BAK;.ASPX;.DESIGN;.IBANK;.LUA;.ASM;.HPP;.VBPROJ;.CSPROJ;.SLN;.CS;.VB;.LNK;.JPG;.JPEG;.RAW;.TIF;.GIF;
.PNG;.BMP;.3DM;.MAX;.ACCDB;.DB;.DBF;.MDB;.PDB;.SQL;.DWG;.DXF;.C;.CPP;.CS;.H;.PHP;.ASP;.RB;.JAVA;.JAR;.CLASS;.PY;.JS;.AAF;.AEP;.AEPX;.PLB;.PREL;.PRPROJ;.AET;.PPJ;.PSD;
.INDD;.INDL;.INDT;.INDB;.INX;.IDML;.PMD;.XQX;.XQX;.AI;.EPS;.PS;.SVG;.SWF;.FLA;.AS3;.AS;.TXT;.DOC;.DOT;.DOCX;.DOCM;.DOTX;.DOTM;.DOCB;.RTF;.WPD;.WPS;.MSG;.PDF;.XLS;
.XLT;.XLM;.XLSX;.XLSM;.XLTX;.XLTM;.XLSB;.XLA;.XLAM;.XLL;.XLW;.PPT;.POT;.PPS;.PPTX;.PPTM;.POTX;.POTM;.PPAM;.PPSX;.PPSM;.SLDX;.SLDM;.WAV;.MP3;.AIF;.IFF;.M3U;.M4U;.MID;
.MPA;.WMA;.RA;.AVI;.MOV;.MP4;.3GP;.MPEG;.3G2;.ASF;.ASX;.FLV;.MPG;.WMV;.VOB;.M3U8;.MKV;.DAT;.CSV;.EFX;.SDF;.VCF;.XML;.SES;.RAR;.ZIP;.7ZIP;.DTB;.BAT;.APK;After encryption, the ransomware will iterate the folders in the same order, placing the ransom note in them (named How Do I Recover My Files (Readme).txt):
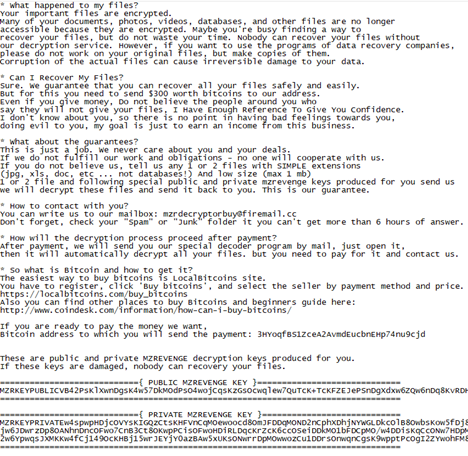
How to use this tool
- Download the decryptor below and save it anywhere on your computer.
Download the MaMoCrypt decryptor
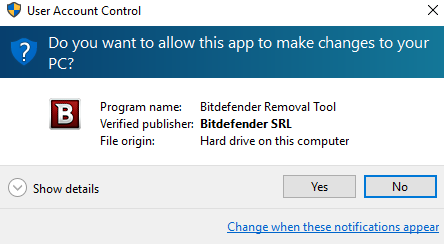
2. Run the tool by double-clicking the BDMaMoDecryptor.exe file and click Yes in the UAC prompt:
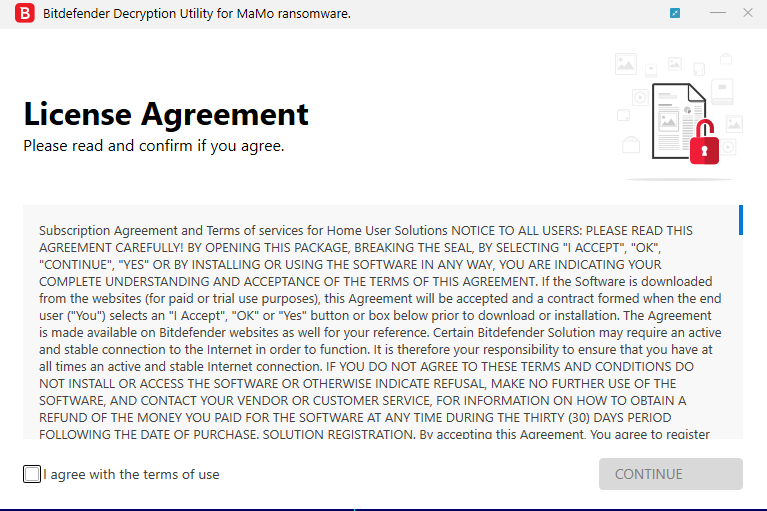
Step 3: Read and accept the End User License Agreement:
Step 4: Because of some specifics of this ransomware family, the tool will scan the system in a particular order rather than allow the user to select a folder with encrypted data. We strongly advise that users select the “Backup files” option.
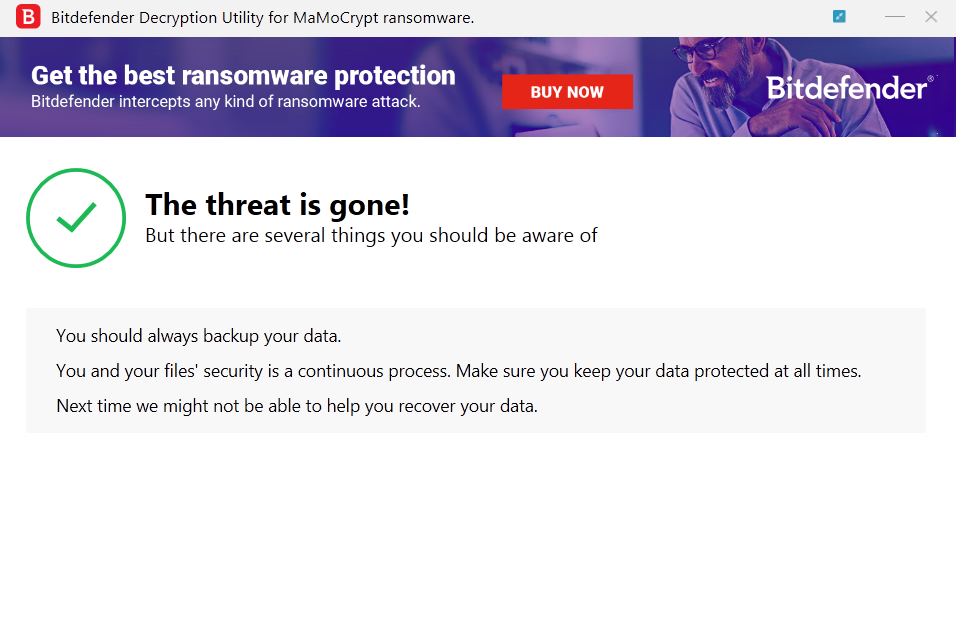
Step 5: Press the “Start Tool” button and let the decryptor finish the job. Your files should now be decrypted. If you encounter any issues, please get in touch with us. If you checked the backup option, you will see both the encrypted and decrypted files. You can also find a log file describing the decryption process in %temp%\BDRemovalTool folder.
tags
Author

The meaning of Bitdefender’s mascot, the Dacian Draco, a symbol that depicts a mythical animal with a wolf’s head and a dragon’s body, is “to watch” and to “guard with a sharp eye.”
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks
















