Mayachok Hooks INT8 to Dodge Emulators

Many new variants of the same bootkits are created simply to avoid detection. Bitdefender anti-malware researchers Cristian Istrate and Marius Tivadar have created a small write-up on the evolution and current status of the Mayachok bootkit:
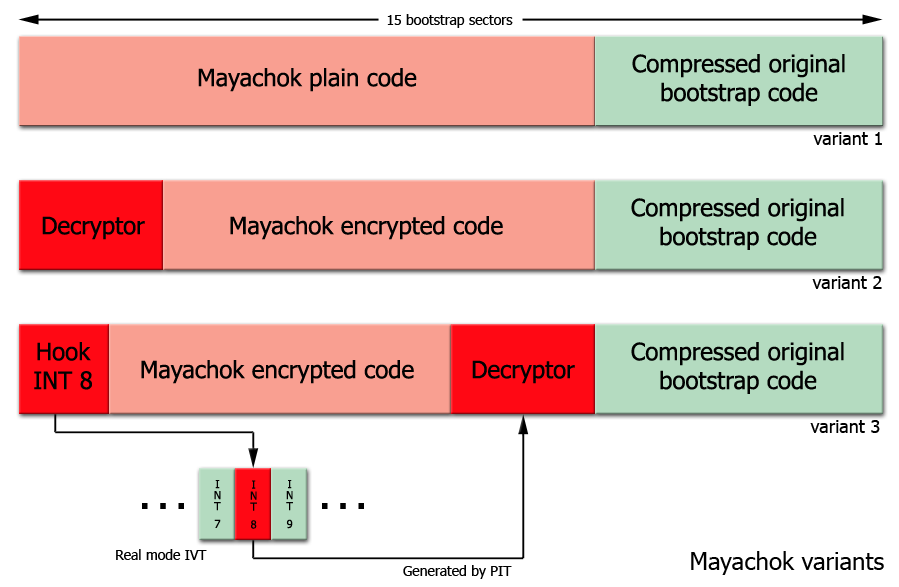
The first version started with its malicious code placed directly in the 15 sectors following the Boot Sector (variant 1 in fig). The second version had its code encrypted and started with a small polymorphic decryption loop (variant 2 in fig). This was done in order to bypass static signature detection. But this version could be generically detected using emulation as there were common blocks of code after decryption.
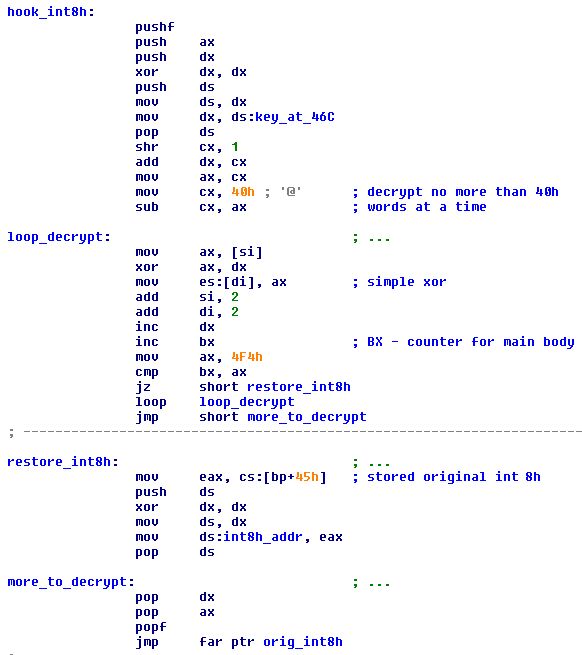
The third version tries to avoid emulation detection also by placing its decryption code in a hook for interrupt 8 (variant 3 in fig).
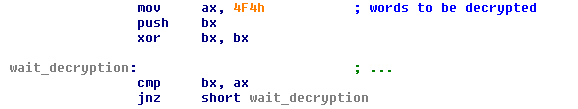
On a typical system, INT 8 is generated by the Programmable Interrupt Timer at about 18.2 times/second and on every tick a dword at address 0040:006Ch will be incremented. The new version of Mayachok starts by placing the decryption hook at INT 8 and initializing the counter at 0040:006Ch.
Then it will wait in a loop until its code is decrypted. In the hook the counter is used as a key for decryption.
If the emulator does not generate INT 8, the malicious code loops indefinitely.
tags
Author

Razvan Stoica is a journalist turned teacher turned publicist and technology evangelist. Recruited by Bitdefender in 2004 to add zest to the company's online presence.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks