MiniDuke - Even Older than we Thought

Bitdefender antimalware researchers have found yet another sample of the MiniDuke malware, only this one is dated June 20, 2011, the oldest found so far.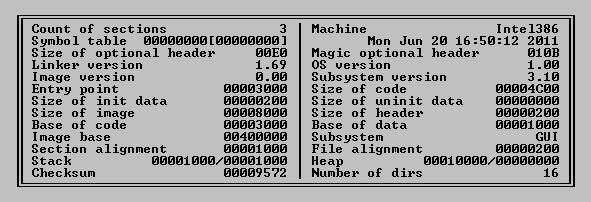
The malware sample is a small executable that drops and loads a .dll. The dll is a little bit different from more recent versions, it has many imports, just as if it was an ordinary program, from kernel32.dll, user32.dll, gdi32.dll and comctl32.dll. Also, the method of computing the system fingerprint is a little different.
Interestingly, the current time/date was then fetched from tycho.usno.navy.mil/cgi-bin/timer.pl (Department of the Navy site).
There is no Google search backup way to contact command and control servers (if connecting to Twitter fails, then nothing happens). So we can see that the use of Google search technique has been introduced after 2011.
There are also new (to us) Twitter indicatives: ObamaApril and Qae9XMs. In this earlier version the malware connects to twitter.com directly, instead of via mobile.twitter.com as in 2012/2013 versions. 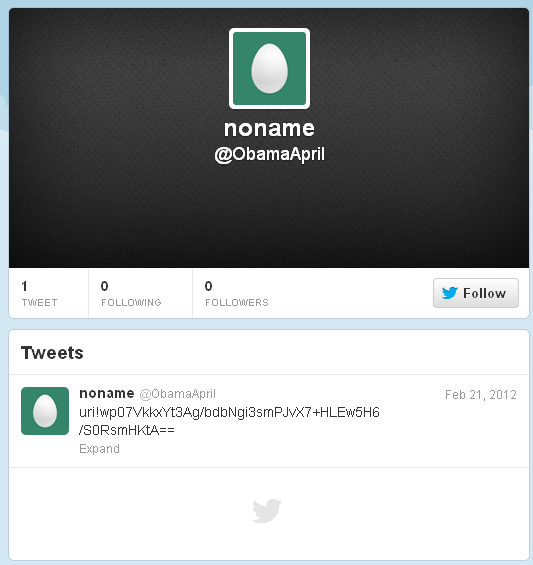
Surprisingly enough, the Twitter account which was used is still active. Its last and single post is from Feb 21, 2012. tweet is uri!wp07VkkxYt3Ag/bdbNgi3smPJvX7+HLEw5H6/S0RsmHKtA== and this decodes to “http://afgcall.com/demo/index.php”, another server that was probably hacked. However, no files have been found on that particular server. This is probably because the malware sample is so old that the command and control server is no longer active.
A removal tool covering all known variants (including this one) has been posted here:
[download id=”3800″]
tags
Author

Razvan Stoica is a journalist turned teacher turned publicist and technology evangelist. Recruited by Bitdefender in 2004 to add zest to the company's online presence.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks
















