Trojan Promises Naked Videos of Facebook Friends

More than 2,000 people have been tricked into installing a Trojan after clicking on a new Facebook scam that promises naked videos of their friends. According to Bitdefender Labs, the countries with the most detected infections are Romania, the UK, Italy, France, Germany, and the US.
The scam has just started to make rounds on the social network and can multiply itself and tag users’ friends extremely quickly. Over 6,000 .tk websites have been registered for malicious purposes. To avoid detection, cyber-criminals vary the scam messages from “user’s name private video” to “user’s name naked video” or “XXX private video”. Malware writers can also redirect users to fake surveys or toolbar, video and converter downloads.
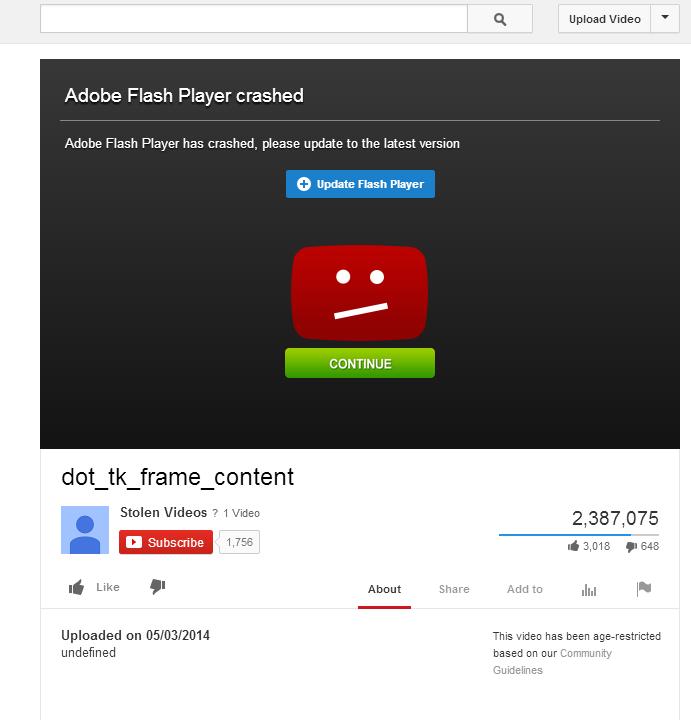
When clicking the link that promises videos ok their friends naked, users are redirected to a fake YouTube website where a “FlashPlayer.exe” file deploys a Trojan. The malware installs a browser extension capable of posting the scam on users’ behalf and stealing their Facebook pictures.
To increase the infection rate, the malware has multiple installation possibilities. Besides the automated and quick drop on the computer or mobile device, it also multiplies itself when users click the fake Adobe Flash Player update.
To make the scam more credible, cyber-criminals faked the number of views of the adult video. Over 2 million users have allegedly clicked on the infected “YouTube” link. To add another touch of realism, the malware creators also added a message that the video is “age-restricted” based on “Community Guidelines.”
Scammers also fake the date they uploaded the malicious video by making it current. Bogus Flash Player installers have been infecting users on Facebook and Twitter for a couple of years.
The malware is detected by antivirus software provider Bitdefender as Trojan.FakeFlash.A (Trojan.GenericKD.1571215), while the fake YouTube link is marked as a fraudulent attempt. For maximum protection, the Bitdefender free application Safego also alerts users about the naked video scam circulating on the social network.
This article is based on the technical information provided courtesy of Octavian MINEA and Cosmin TARSICHI, Bitdefender Malware Researchers.
All product and company names mentioned herein are for identification purposes only and are the property of, and may be trademarks of, their respective owners.
tags
Author
I'm a down-to-earth journalist, who's always on to a cyber-trendy story. Proud mother of one, I cover parental control topics and like to let words and facts speak for themselves.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks