Account Takeover Attacks on Social Media: A Rising Threat for Content Creators and Influencers

Note: All product and company names mentioned herein are for identification purposes only and are the property of, and may be trademarks of, their respective owners.
In 2024 and continuing into 2025, social media platforms were prime targets for cybercriminals, with content creators facing the brunt of the malicious attacks, including a surge in account takeovers, malicious live streams, and sophisticated phishing campaigns.
Bitdefender Labs has been at the forefront in analyzing these threats, and the numbers paint a stark picture of a rapidly evolving threat landscape that harms the livelihood of both content creators and followers.
Let’s examine the most striking trends from 2024, along with key attack methods and real-world examples of how cybercriminals are compromising creator accounts.
Creator Accounts and the Threat Landscape
Key insights on attacks targeting content creators over the past 12 months, according to Bitdefender Labs researchers:
- Over 9,000 malicious livestreams were detected on YouTube. These streams often appear legitimate at first glance, but they are controlled by hackers who have rebranded compromised channels.
- 28.1 million – the highest subscriber count of a compromised YouTube account.
- 12.4 billion – highest total view count for a compromised account. The staggering number underscores the global reach that threat actors can access. If cybercriminals convert just 1% of those views, that equates to a staggering 124 million potential victims exposed to scams, malware, or data theft.
- 350+ malicious domains promoted via malicious livestreams were detected. Cybercriminals commonly direct viewers to fraudulent domains to steal credentials, cryptocurrencies, or personal information.
No content creator or influencer is immune, with established channels with millions of subscribers falling victim to these sophisticated attacks.
Why Content Creators Are Prime Targets
Content creators have a high degree of online visibility, relying mostly on public engagement to ensure their success. This means that they are more susceptible to being approached by fans, followers, and “sponsors.” Many creators also manage multiple social media platforms (YouTube, Instagram, Facebook, TikTok, Twitch), sometimes, under the same or interconnected credentials, which just expands the attack surface. For example, a breach on one platform can easily expand to others. Once compromised, cybercriminals can quickly exploit a creator’s large following, using malicious livestreams or fraudulent links to potentially reach thousands or even millions of viewers.
Tactics Employed by Malicious Actors
Rebranding of YouTube Accounts and Malicious Livestreaming
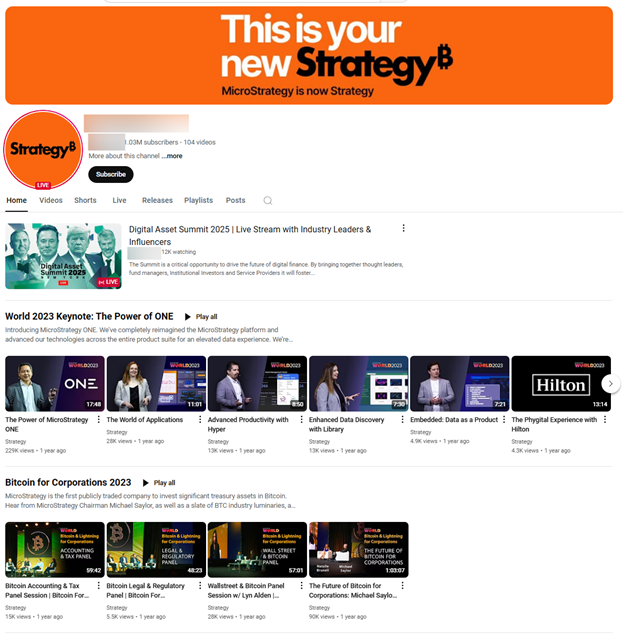
One of the most common tactics employed by cybercriminals involves taking over an existing channel and completely transforming it by either setting original videos to private or deleting them entirely. The metamorphosis includes changing channel names, handles, avatars and playlists to reflect the impersonated brand individual. To monetize newly captured accounts, attackers host fake livestreams featuring prominent figures like Brad Garlinghouse (XRP), Elon Musk (Tesla, US elections), or Michael Saylor (MicroStrategy), aiming to trick viewers into visiting malicious domains.
Some of the most commonly impersonated channel names in 2024 include:
- Tesla
- MicroStrategy
- Ripple
- MicroStrategy US
- Tesla US
- Tesla Live
- SpaceX
- Tesla News
- Cardano ADA
- Michael Saylor
- TesIa Official (notice the capital ‘i’ in place of lowercase ‘l’)
- Bitcoin Magazine
- SpaceX Live
Engaging in Timely Attacks Linked to Big Events
Cybercriminals ramp up attacks during periods of intense media buzz, such as the US Elections, high-profile lawsuits like the XRP trial with the SEC, Bitcoin ETF launches, major Apple keynotes, or SpaceX rocket events. Whenever these hot topics dominate online conversations, scammers exploit the spike in online traffic.
Malicious Sponsorship Offers
One of the most common ways creators get hacked is through fake sponsorship proposals that appear to be from reputable brands (like Razer, DocuSign, Notion, Spotify, etc.). Opening or downloading these “offers” can lead to malware infection, specifically designed to steal social media credentials.
Malvertising on Social Media
Attackers also employ malicious advertisements (malvertising) to take over accounts. These ads often promote “exclusive” software such as AI-powered video editors or even fake versions of popular games (e.g., GTA VI, League of Legends). Once downloaded, the malware scours systems for login credentials.
Bitdefender Labs covered several real-world cases in articles, such as:
- Global malvertising campaign targeting Meta Business Pages
- Fake Bitwarden extension
- AI-related software scams
- Fake GTA VI downloads
- Fake League of Legends software
The Instagram Angle: Phishing and Social Engineering
While YouTube account hijacks and malicious livestreams have been in the spotlight, Instagram creators are also targets:
- Phishing Emails and Messages
Hackers impersonate Meta/Instagram Security, urging creators to click a link to “verify” or “secure” their account. These phishing sites clone the real Instagram login page, capturing usernames and passwords. - Phone Number and SMS Codes
Social engineers pose as fans or acquaintances, requesting the creator’s phone number. They then send a password reset code (or an email change request) and manipulate the victim into sharing the verification code. - Fake Contests and Votes
Hackers claim there’s a contest or giveaway that requires a “vote” via email confirmation, tricking creators into unwittingly authorizing changes to their accounts.
How 2024 Trends Have Continued into Early 2025
While 2024 saw rampant account takeovers and malicious livestreams, Bitdefender Labs researcher Ionuț Baltariu says that these tactics have escalated and evolved in early 2025. After taking over creator accounts, malicious actors exploited the following events to target internet users:
High-Profile Exploits at Major CS2 Tournaments
Attackers have targeted Counter-Strike 2 events, hijacking channels to stream fake tournament coverage. They embed scam links in descriptions or live chats, often promoting crypto giveaways and CS2 skins
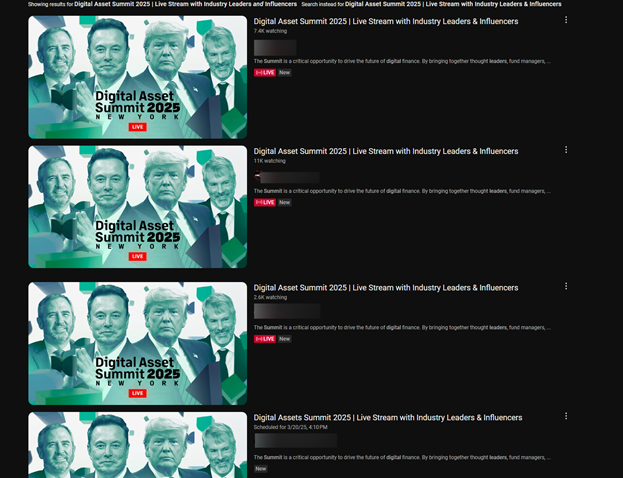
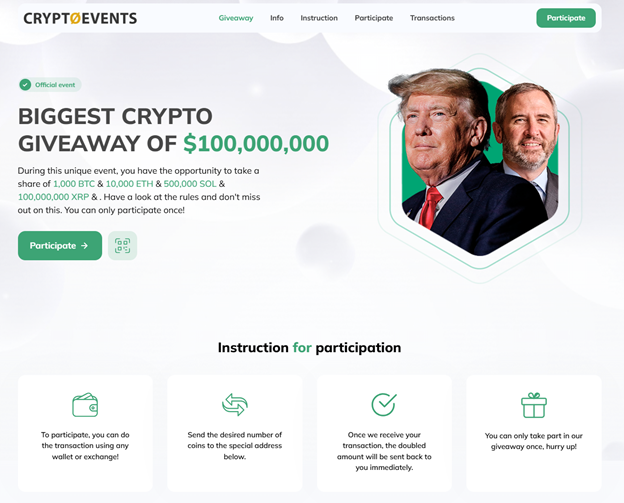
Donald Trump & Elon Musk Deepfakes
Cybercriminals used looped “podcast”-style formats featuring the likeness and voice of public figures like Donald Trump and Elon Musk. These deepfake streams often push crypto scams, direct viewers to malicious websites, or trick them into sharing private data.
Giveaway Scams
Building on a trend from 2024, scammers leveraged the hype around major personalities or events to host bogus giveaways. Victims were asked to send cryptocurrency in exchange for the promise of larger returns—or provide personal details in exchange for “rewards.”
White House Crypto Summit (March 2025)
During this widely covered summit, malicious livestreams disguised as official coverage urged viewers to sign up for “exclusive airdrops.”
Ongoing XRP News & SEC Updates
Attackers exploited the hype surrounding XRP News & SEC Updates with fraudulent livestreams.

Emerging Tactics and What to Watch For
While much has already transpired in the opening months of 2025, Baltariu expects threat actors to continue and expand their attacks via:
- Deepfake “Podcasts”. Attackers are expected to produce increasingly sophisticated deepfake interviews or talk shows featuring recognizable personalities to enhance credibility and lure viewers.
- Malware Hidden in Fake Software, Game Cheats & Cracks
Many creators are drawn to reviewing or demoing “exciting new tools.” Hackers will continue leveraging fake or “cracked” software, game cheats, and other downloads to deliver info stealers and remote access trojans. - Bypassing Geo-Restrictions. Tools or tutorials claiming to circumvent local bans or restricted services can be laden with malware, granting attackers illicit access to victims’ devices.
Protecting Your Channel means Protecting Your Community and Livelihood
- Enable Multi-Factor Authentication (MFA). This is the first line of defense. Even if your credentials are compromised, MFA can prevent unauthorized logins via credential-stuffing attacks.
- Scrutinize Sponsorship Offers by always verifying domain names and email addresses. If a sponsorship seems too good to be true (or is oddly relevant to your niche but from an unknown brand), proceed cautiously. Use a sandbox or virtual environment to open suspicious files if you have the technical expertise.
- Be Wary of “Too Timely” Offers. If you receive a sponsorship related to trending events you’ve covered (like cryptocurrency price surges), double-check the legitimacy. Attackers often exploit trending topics.
- Monitor Account Activity. Regularly check for unusual logins, unauthorized changes, or suspicious new uploads. Many social media platforms allow you to view recent account activity in your security settings.
- Educate Your Team. If you have editors, managers, or external collaborators, make sure they’re aware of these threats. A single click from one team member can expose your entire channel and threaten your livelihood.
- Follow Official Channels for Updates. Platforms like YouTube, Facebook, and Instagram often publish security bulletins. Bitdefender Labs and other cybersecurity outlets also share insights and indicators of compromise that can help you stay one step ahead of these attacks.
Pro Tip: Use Bitdefender Security for Creators
Bitdefender Security for Creators is a comprehensive cybersecurity suite designed specifically to protect YouTube content creators. This all-in-one security suite safeguards accounts and devices against a wide range of digital threats with feature such as:
- YouTube Channel Protection: Monitors your channel 24/7 for account takeover attempts and provides a guided recovery process if compromised.
- Account Health Monitoring: Continuously scans for security vulnerabilities and potential breaches.
- Guided Recovery: A step-by-step guide to help you regain control of a hacked account.
- Scam Guard: Flags suspicious emails from fraudulent sponsors, preventing phishing attacks.
- Device Protection: Secures login credentials, protects against malware, and ensures safe public Wi-Fi usage.
- Team Shield: Extends protection to all team members with access to your YouTube account.
- Live Reports: Provides real-time security insights, tracking account performance and risks.
Stay safe, stay informed, and remember: a few moments of caution can save years of hard work.
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







