Bitdefender detects novel spam trends as fraudsters build repertoire of Ukraine charity scams

Bitdefender researchers have been keeping a close eye on spam campaigns piggybacking on the war in Ukraine in recent weeks. Since the beginning of the Russian invasion of Ukraine, our antispam filters have sniffed out tens of thousands of phony donation emails and malicious phishing campaigns targeting digital citizens from across the globe in an attempt to steal money and compromise their devices.
Bitdefender’s latest analysis of Ukraine-related spam trends shows that cybercrooks are not backing down and continue to exploit the crisis, tailoring their schemes for maximum impact on targets.
Campaign 1: The thoughtful plagiarist
It’s official: scammers do read the news! The latest iteration of Ukraine donations scams might have passed for the real deal if fraudsters had paid more attention to detail.
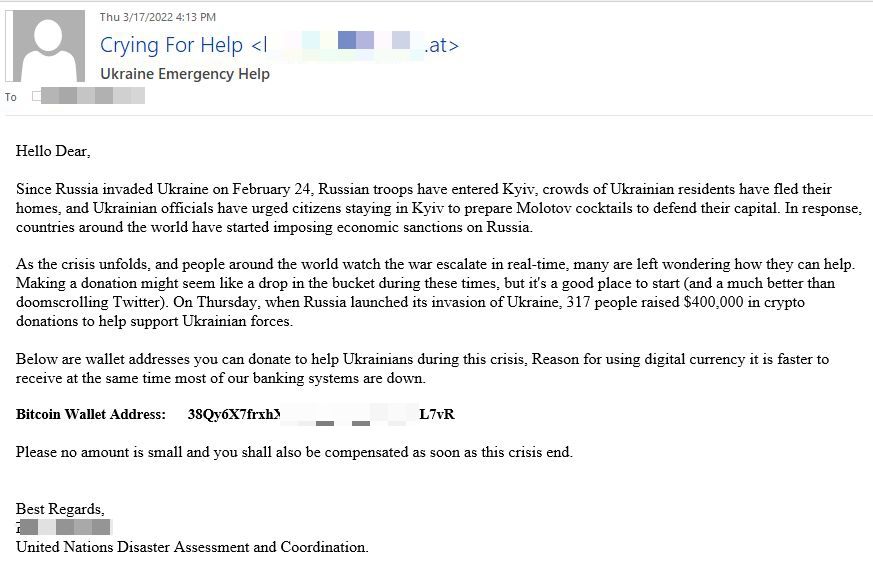
On March 18, the Bitdefender Antispam Lab caught another email-based charity scam asking recipients to help with the humanitarian crisis by sending donations to a Bitcoin wallet.
86% of the fraudulent messages were sent from IP addresses in Lithuania, ending up in inboxes in South Korea (40%), Czech Republic (16%), Germany (7%), the US and UK (5% each), India (4%) and Romania and Italia (2% each).
What makes the latest attempt at defrauding big-hearted internet users stand out is the lack of grammar mistakes at the start of their plea for help.
They begin with a short introduction to the Russian invasion of Ukraine that caught our attention. The two paragraphs are perfectly written; so we did some digging. It appears the scammers have started to plagiarize the work of journalists to legitimize their dirty work.
The passages found below were copy-pasted from an article written by a journalist at Fortune.com on Feb 25.
“Since Russia invaded Ukraine on February 24, Russian troops have entered Kyiv, crowds of Ukrainian residents have fled their homes, and Ukrainian officials have urged citizens staying in Kyiv to prepare Molotov cocktails to defend their capital. In response, countries around the world have started imposing economic sanctions on Russia.
As the crisis unfolds, and people around the world watch the war escalate in real-time, many are left wondering how they can help. Making a donation might seem like a drop in the bucket during these times, but it's a good place to start (and a much better than doomscrolling Twitter). On Thursday, when Russia launched its invasion of Ukraine, 317 people raised $400,000 in crypto donations to help support Ukrainian forces.”
Where it all went south
The first half of the scam message may not raise any red flags, but the last two sentences of the email do. The spammers are not native English speakers and continue to advance crypto wallets as their main donation method. In addition to the poorly drafted request for digital currencies, the scammers add an interesting twist: they promise you compensation “as soon as the crisis end.”
Campaign 2: A change in tactics
Media coverage on Ukraine charity scams have taken off since the beginning of March, and increased consumer awareness of the subject has likely influenced spammers’ strategies.
The fraudsters behind this next scam impersonate The Courage Fund, a Singapore-based charity foundation established in 2003 when the country was hit by the SARS outbreak. Unlike previously reported schemes which incorporated images of the Ukrainian flag next to fraudulent cryptocurrency wallet addresses, spammers behind this campaign take an alternative route - they ask recipients to contact a GMAIL address.
Half of the spam emails originate from IP addresses in South Africa, reaching users in the US (33%), the UK (33%) and Germany (24%).
Once again, scammers use official data on Ukrainian casualties and refugees, and cite a couple of organizations that have publicly announced humanitarian aid and donations to help war victims.
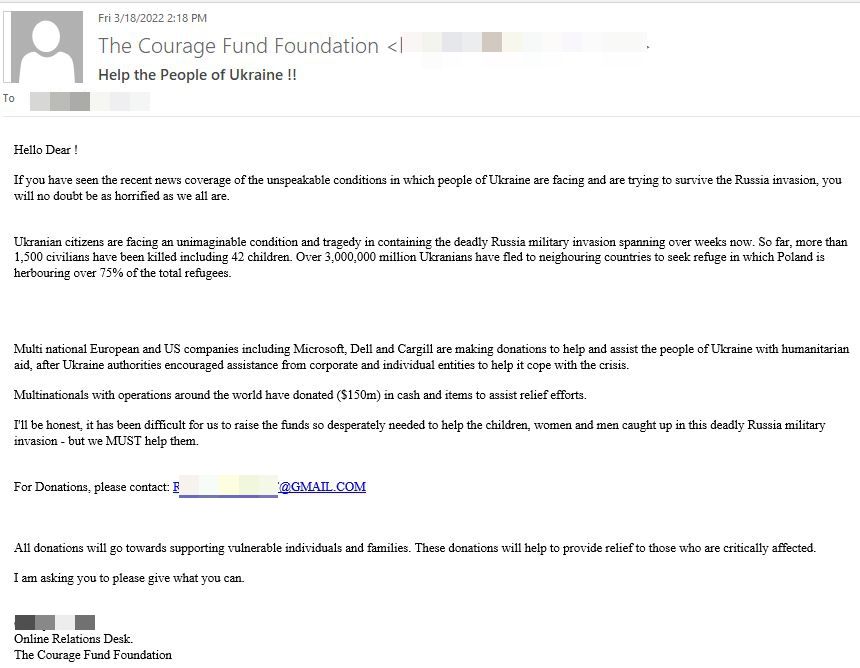
It’s not clear how the cyberthieves will attempt to steal the money of users who fall into this trap. They could ask recipients to wire money, send gift cards or send cryptocurrency. As far as we’re concerned, users should not interact with such correspondence, not even if they know the email is fake.
Campaign 3: Fraudster serve a cloned website version of United Help Ukraine
A novel approach at swindling good Samaritans was spotted by Bitdefender researchers on March 22. The threat actors behind this campaign go way past any previous nickel-and-dime antics, impersonating the United Help Ukraine organization. Spammers are using IP addresses in the US to deliver this scam across Europe and North America.
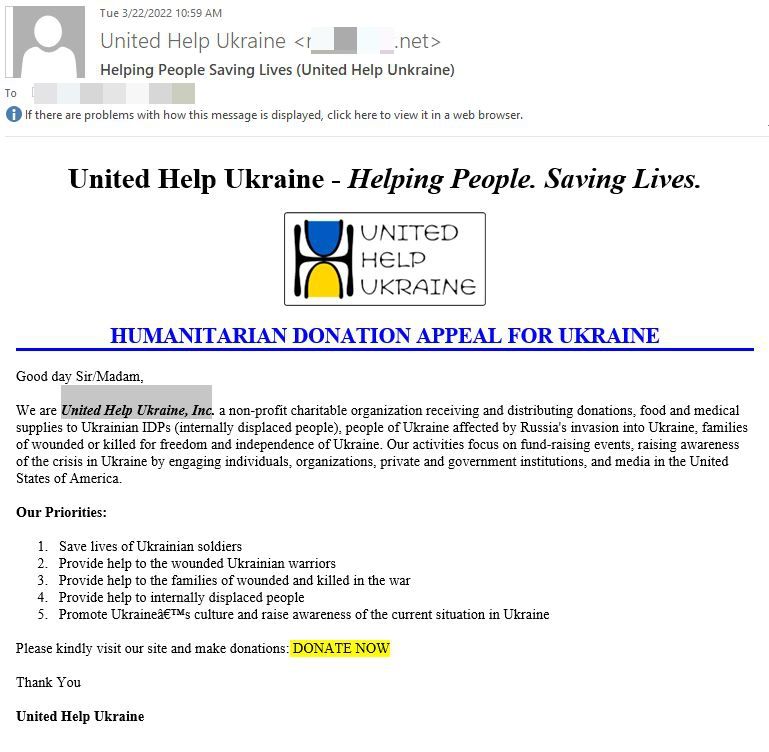
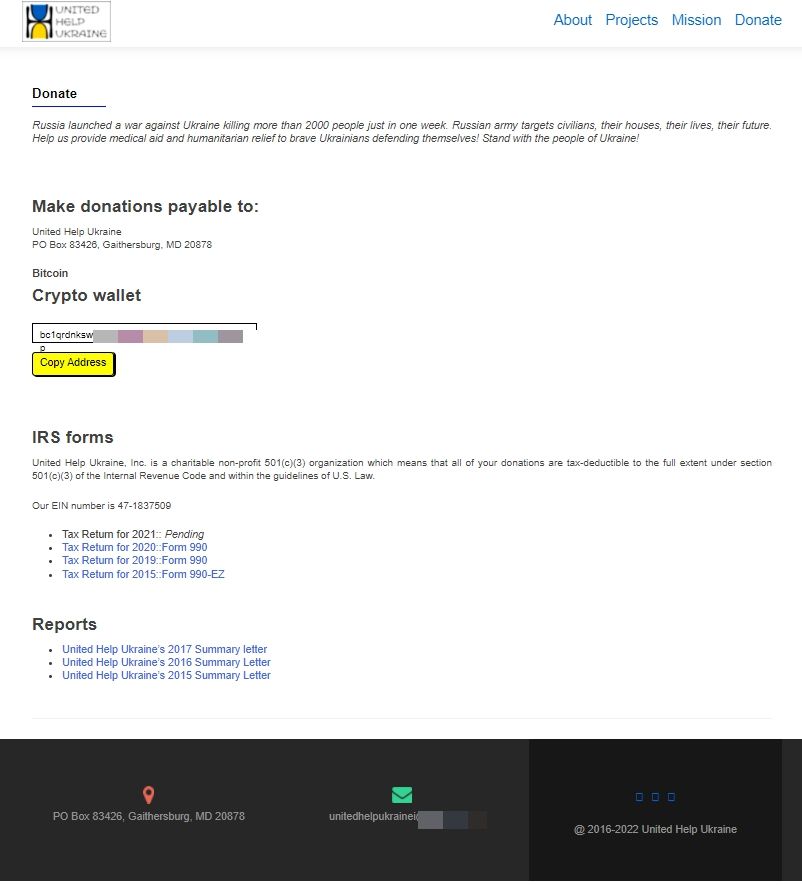
The DONATE NOW button sends recipients to a cloned version of the official United Help Ukraine Website.
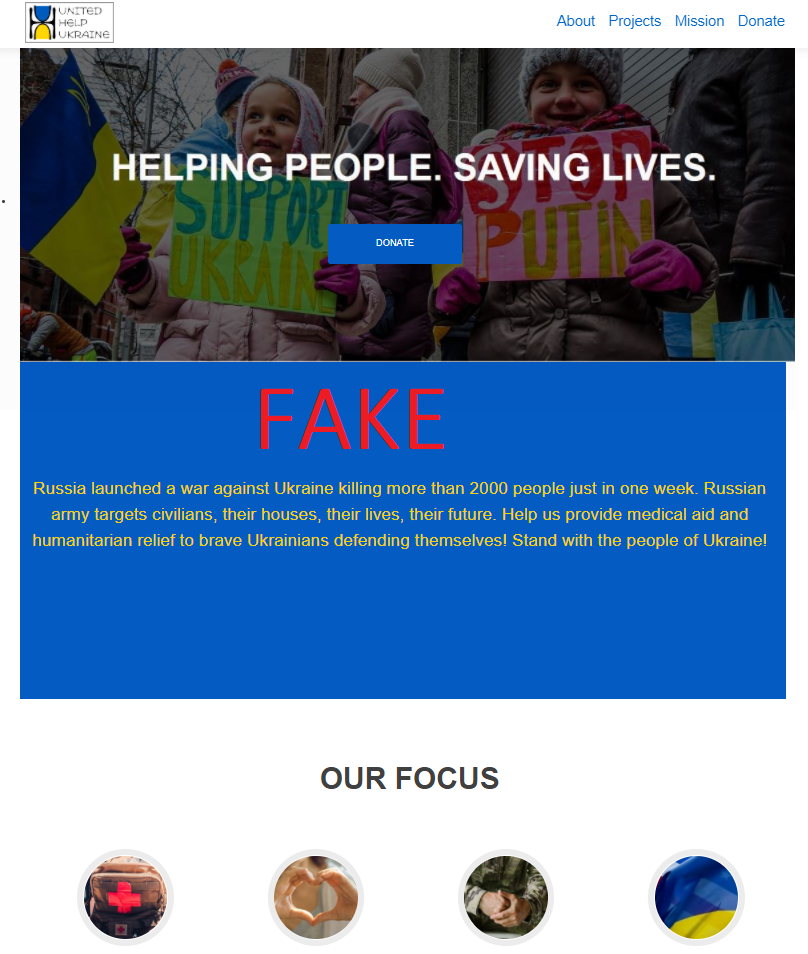
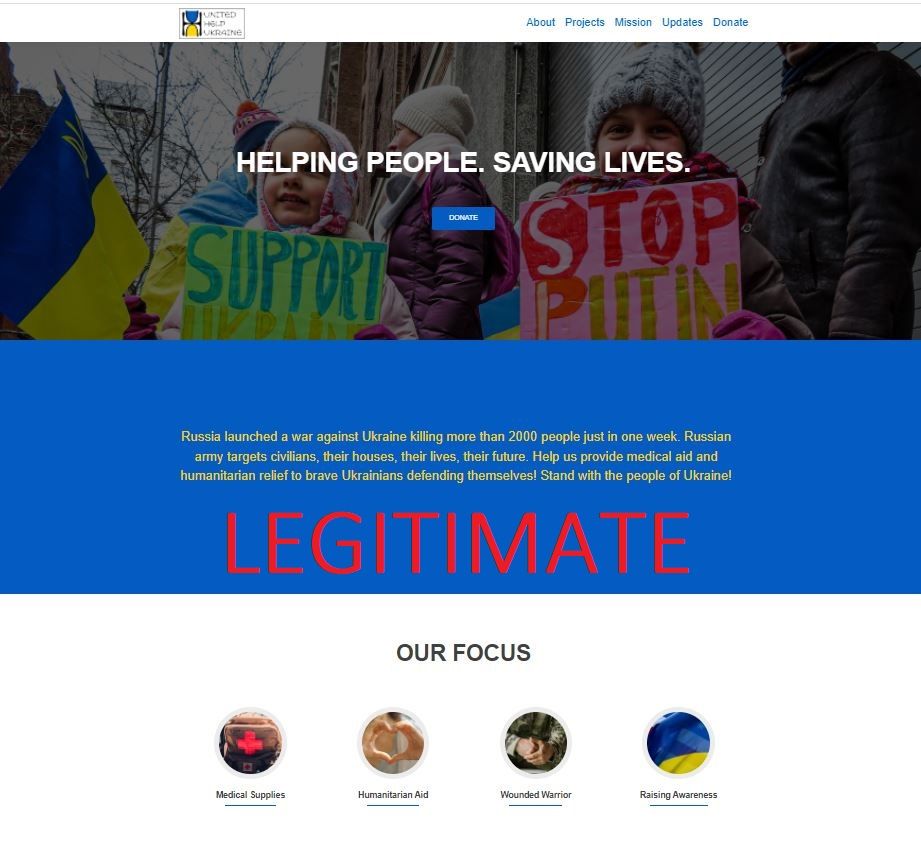
The fake website offers users a single donation method in the form of a crypto wallet address, and it closely resembles the official Donate page of the non-profit charitable organization.
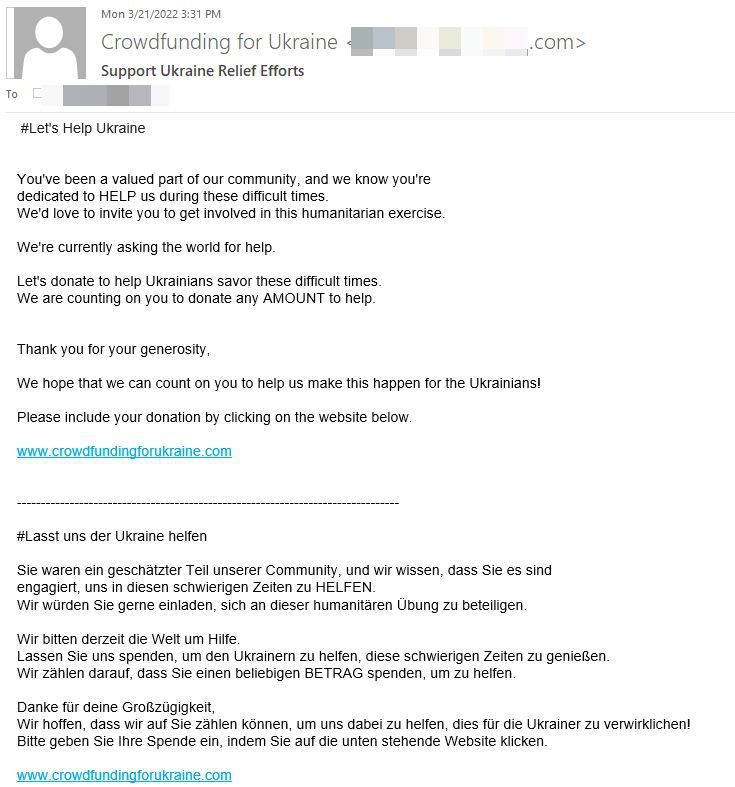
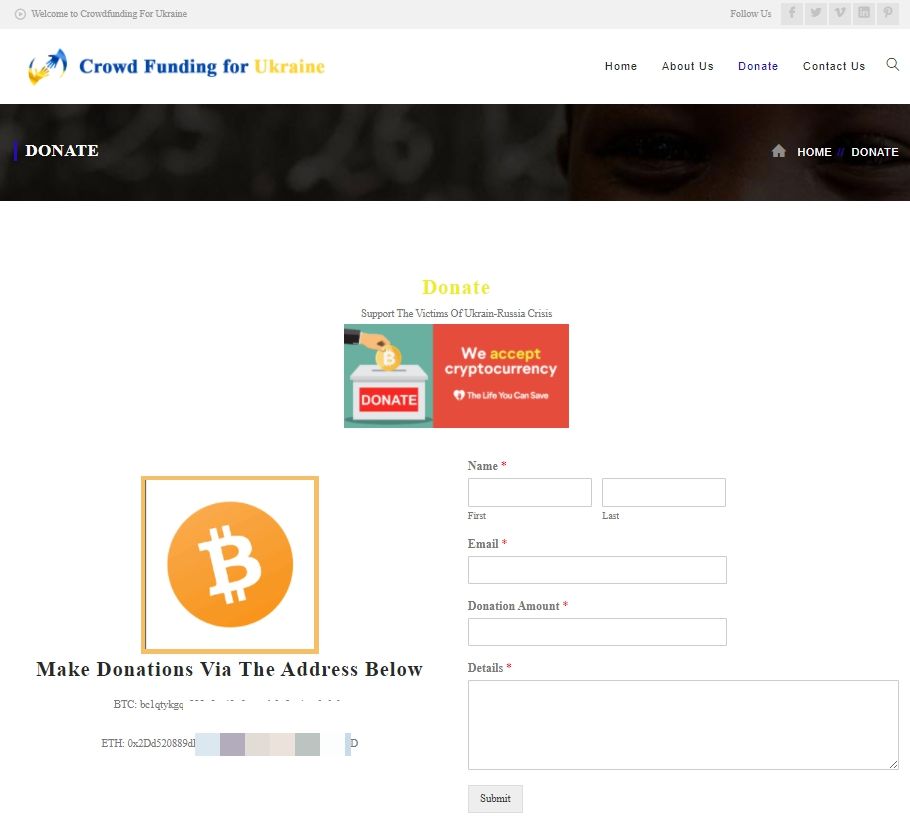
Campaign 4: Phony Crowdfunding for Ukraine
Scammers are also pretending to raise donations for Ukraine via a fake crowdfunding page. The emails were sent from IP addresses in the US and Japan. Although they contain four separate messages redacted in English, German, French and Spanish, 40% of the bogus emails ended up in the Inboxes of Belarus citizens. An additional 19% targeted users in Japan, 15% in South Korea, 5% in the US, 4% in Austria, 3% in Germany, and 2% in the UK.


The crowdfunding website is already blocked by Bitdefender anti-phishing and anti-fraud filters. It is well crafted and could potentially fool unsuspecting users easily.
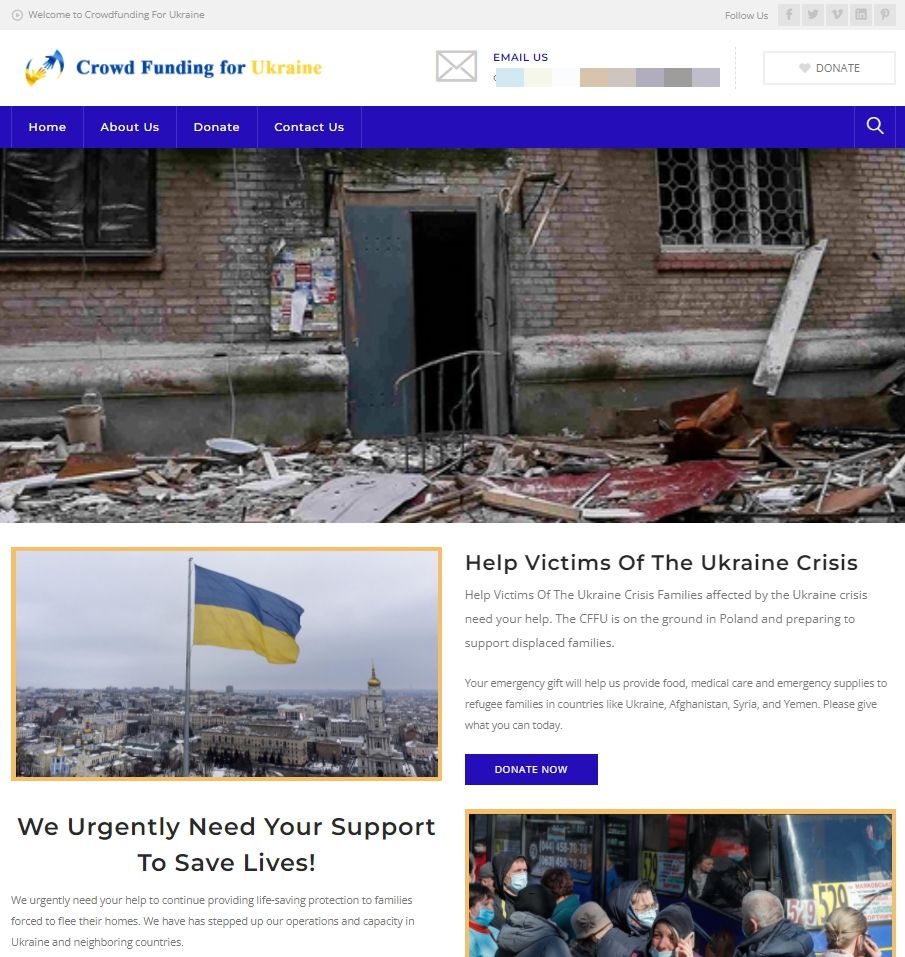
The phishing website offers a donate section with two crypto wallet addresses in Bitcoin and Ethereum. They can also fill out a form with their name, email address, and amount, offering the scammers more leverage in future attacks.
We encourage everybody who wants to help those in need to closely inspect all communications regarding charitable organizations before donating. To learn more about how to spot and protect against scams, please check our dedicated guide.
Stay Safe!
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks




